Are you concerned about the newest online attack targeting your business’s top executives? Do you want to know more on how to protect yourself, and your company’s confidential information, from whaling phishing attempts?
With an increased amount of attackers specifically targeting those in powerful positions, it is important for cyber security professionals like yourself to understand what whaling phishing is and how to effectively shield against it.
Keep reading this blog post to learn more about this dangerous type of scam!
What is whaling phishing?
Whaling phishing is a form of cyber-attack that targets high-level executives within organisations. Unlike regular phishing, which usually targets a large number of individuals, whaling phishing focuses on a specific individual who has access to sensitive information or can make important financial decisions.
Cybercriminals use social engineering to trick their targets into revealing confidential information or transferring money to fraudulent accounts.
These attacks often involve the use of fake emails that appear to come from a trusted source, such as a senior executive or a business partner.
Whaling phishing attacks can be difficult to detect, so it's important for organisations to implement strong security measures and educate their employees on how to identify and avoid these types of scams.
Whaling is another form of phishing that often targets senior management – it’s a type of social engineering that chooses a ‘High Level Target’ and attempts to encourage the victim to perform a secondary action such as, divulge sensitive information or wire transfer funds.
These types of phishing scams are highly targeted, sophisticated, researched and difficult to detect.
Typically, they contain personalised information about the target or organisation, combined with a formal, corporate tone of voice to throw you off guard.
Whaling phishing is one of the biggest risks facing businesses as these types of phishing scams do not require a great deal of technical knowledge but can deliver huge returns.
Whaling phishing emails often consist of:
- A sense of urgency
- Personalised information about the target and/or organisation
- Corporate/business tone of voice and jargon
Whaling Phishing Examples
Here are three whale phishing examples:
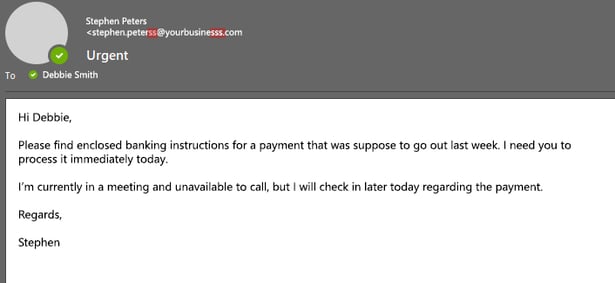
Example 1 - Whaling phishing can appear to come from internal employees:
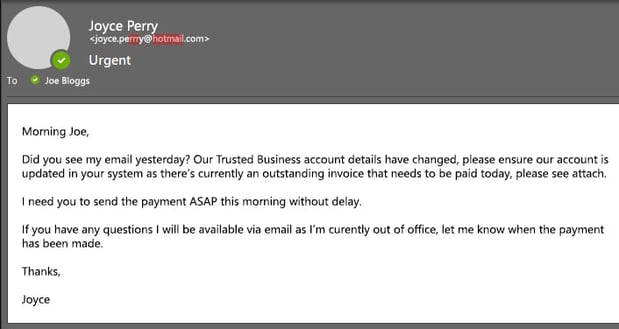
Example 2 - Cyber criminals may try to impersonate your customers or clients:
Example 3 - Spotify Email Spoofing:

As you can see in example 3, both emails are very similar and at first glance, you wouldn't think anything was awry until you check the sender email address.
But as you can see, the fake email (left) has a sense of urgency to it, they know the user probably uses Spotify and it features a corporate tone of voice with the same wording 'We're always here to help if you need it' that the real email (right) features.
How to prevent Whaling Phishing Attack?
Here are 7 ways you can prevent whaling phishing attack:
1. Double check email addresses
As you can see from the examples above, the email may appear to be from a legitimate source, but after careful inspection, there may be additional letters, numbers or different email providers.
2. Train your employees
Provide training for your staff about whaling attacks and how to identify phishing emails.
3. Phishing Testing
Test your staff with fake phishing emails to see how many believe an email is legitimate, how many click on links or reply to the email - then provide them with the results and additional training if needed.
4. Multi-Step Verification
Enable multi-step verification for all requests for sensitive data or wire transfers.
5. Follow up phone call
If you're unsure about an email, speak to the colleague or customer who sent it. Don't reply or use the contact information from the email.
6. Do not click links in email
If you want to check your account on the website the email is referencing, open it in your web browser separately - do not click links in the email as they usually are followed by a fake website that's designed to steal your data as you try to log in.
7. Report
Report the phishing email to your IT department - this may be one in a hundred emails that have been sent to your organisation and others may not realise it isn't genuine.
What is the difference between phishing and whaling?
While these terms are often used interchangeably, there is a fundamental difference between them.
Phishing is a type of online scam where cyber criminals impersonate a legitimate organisation or individual in order to obtain sensitive information such as passwords and credit card details.
Whaling, on the other hand, is a type of phishing that targets high-profile executives, typically in the form of CEO fraud.
As the stakes are higher in whaling attacks, cyber criminals invest more time and effort in researching their target and customising the attack to make it appear more legitimate.
It is important to be aware of the difference between phishing and whaling to ensure that we stay safe online.
What is the difference between whaling and spear phishing?
Whaling and spear phishing are two terms that often get conflated, but in reality, they are distinct forms of cybercrime. The difference between whaling and spear phishing mainly lies in their targets.
Whaling refers to targeted attacks on high-profile individuals in an organisation, such as CEOs or board members. These attacks are intended to collect sensitive information or gain access to financial resources.
Spear phishing, on the other hand, is a more generalised form of phishing focused on individuals or small groups, designed to trick them into revealing their personal or financial information.
Both forms of attack rely on the elements of social engineering, but the distinction between them can help raise awareness among businesses, and individuals, about the need to be more vigilant about online security threats.
Read our blog on frequently asked questions about phishing for more answers to your questions related to whale phishing.
How can Aztech help?
Aztech offer a range of cyber security services to provide you with a multi-layered IT security solution for your business - our solution is designed to make you feel assured your cyber security is being managed proactively and appropriately.
We can provide training for your staff on the warnings signs of potential cyber attacks and keep you up-to-date with the latest threats.
If you'd like to find out more, get in touch and see how we can help you protect your business against the latest cyber threats.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)