If you work in cyber security, then you know how important it is to be aware of the latest threats and techniques used by cybercriminals.
Phishing attacks are one of the most common and dangerous types of cyber attacks, so having a good understanding of them can help keep your organisation safe.
In this blog post, we'll go over some frequently asked questions about phishing that will help you gain a better understanding of what it is and how to prevent it from happening in your business.
63 Latest Phishing Related FAQs 2023 Updated
1. What is the meaning of phishing?
Phishing is a deceptive technique used by cybercriminals to gain access to sensitive and valuable information.
The term "phishing" comes from the analogy of fishing: in the same way that fishermen use bait to lure fish, phishers use fraudulent messages, emails, and websites to lure unsuspecting users into giving away their personal information, such as their passwords, credit card numbers and social security numbers.
2. What is an example of phishing?
The commonly witnessed example of phishing by most people is a phone call scam for OTP. Google Pay OTP code scam and OLX OTP code scam are the most popular examples of phishing.
3. What are the 4 types of phishing?
The 4 types of phishing are spear phishing, clone phishing, whaling, and phishing via social media.
4. Which is a phishing email?
A Phishing email is when the recipient believes that the message is legitimate and trustworthy.
5. What are the 3 steps of a phishing attack?
The 3 steps of a phishing attack are:
In the first step, the attacker creates an email, text or social media message that appears to be from a legitimate source, such as a bank or a well-known company.
In the second step, they use social engineering tactics to encourage the victim to click a link or download an attachment, which leads them to a fake webpage or malicious software.
In the third step, the victim is prompted to provide sensitive information such as their username and password.
6. What are the 4 steps to protect yourself from phishing attacks?
The 4 steps to protect yourself from phishing attacks are:
Firstly, always double-check the sender of any email you receive and ensure that it is legitimate.
Secondly, avoid clicking on any suspicious links or opening any suspicious attachments.
Thirdly, strengthen your password and enable two-factor authentication wherever possible.
Fourth, always keep your devices and software updated to make sure you have the latest security patches installed.
7. How do you deal with phishing?
To deal with phishing, avoid clicking on suspicious links or downloading attachments from unknown sources. Always verify the authenticity of the sender and message before taking any action.
8. What is most commonly asked for in a phishing attempt?
The most commonly asked for in a phishing attempt is your login credentials. According to a recent study, the most commonly requested piece of information is your login credentials, followed closely by credit card details, social security numbers, and other personal information.
9. What is spear phishing?
Spear phishing is a type of cyber attack that targets specific individuals or organisations. In spear phishing, attackers send tailored phishing emails to specific victims to lure them into revealing their sensitive information.
10. What is a phishing attack?
Simply put, a phishing attack is defined as a fraudulent attempt by hackers to obtain sensitive information such as passwords, credit card details, and other personal data by posing as legitimate entities.
11. What is phishing in computers?
Phishing in computers means the attacks include email phishing, phone phishing, and text message phishing.
12. What is a phishing scam?
A phishing scam is a type of online fraud that involves tricking individuals into revealing sensitive information, such as usernames, passwords, and credit card details.
Criminals typically use email, social media, or text messages to lure victims into giving up this information, often by posing as a trustworthy person or organisation.
13. What is smishing and phishing?
Smishing is a type of phishing scam that involves sending text messages with a fake or malicious link that, once clicked, can cause harm to your device, or infect it with malware.
On the other hand, phishing is an attempt to deceive individuals into sharing sensitive information, such as passwords or credit card numbers, by posing as a trustworthy entity through email or other online messaging platforms.
14. What is the difference between blagging and phishing?
Phishing relies on deceptive electronic communication (emails, websites) to trick individuals into revealing personal information whereas, blagging involves obtaining information through social engineering tactics, like impersonation or pretending to have authority, often in person or over the phone.
Example of Phishing: An individual receives an email that appears to be from their bank, requesting them to update their account information by clicking on a link provided in the email. The link leads to a fake website designed to steal the individual's login credentials.
Example of Blagging: A person calls a company's customer service hotline and pretends to be an employee from another department, claiming they need access to sensitive information for a supposed urgent project. They use this ruse to convince the customer service representative to provide the information without proper verification.
15. What is spear phishing in cyber security?
In cyber security, spear phishing is a type of targeted attack that involves spoofing an email address to make it look like it's from a certain person or organisation.
16. What is phishing, smishing and vishing?
Phishing is one of the most common types of attacks, where scammers send fraudulent emails or messages to trick you into revealing personal information. On the other hand, smishing is similar, though the scammer attempts to do so through text messages. Vishing, similarly, is a type of social engineering where scammers use phone calls to obtain sensitive information from you.
17. What is a common indicator of a phishing attempt?
A common indicator of a phishing attempt is an unsolicited email or message that requires immediate action. Scammers use a sense of urgency to trick their victims into clicking on links or downloading attachments that could harm their devices or steal their sensitive data. Additionally, check for the sender's email address or website domain, which may be slightly altered or fake.
18. What is whaling phishing?
Whaling phishing is a type of cyber-attack in which the attacker uses social engineering techniques, such as researching the target's personal and professional information, to create a convincing email or message that appears to be from a legitimate source.
In whaling phishing, cybercriminal targets high-ranking individuals or executives within an organisation.
19. What is angler phishing?
Angler phishing is a type of phishing attack that targets social media users. It involves creating a fake website that mimics a legitimate one and then luring users to enter their login credentials.
The attackers then harvest these credentials and use them to spread the scam to the victim’s friends and family.
20. What is online phishing?
Online phishing is a type of cybercrime that involves stealing personal information such as usernames, passwords, and credit card numbers.
Cybercriminals use various tactics, including fake emails, websites, and even social media to trick individuals into giving away their personal information.
This type of online scam can be difficult to detect, so it's crucial to stay vigilant when browsing the internet.
21. What is a phishing link?
In simple terms, a phishing link is a fraudulent website link that is designed to trick you into revealing personal information, such as passwords or credit card numbers. These links are often disguised as legitimate websites or emails and can be very convincing, making it easy for unsuspecting people to fall victim to scams.
22. How to prevent a phishing link?
To avoid falling victim to a phishing link, exercise caution when clicking on links, particularly those from unknown sources. Always verify the URL to ensure it directs you to a legitimate website before sharing any personal information.
23. What is the most common example of phishing?
The most common example of phishing is PayPal Scam. Other examples include Google Docs Scam, Email Account Upgrade Scam, Message from HR Scam, Dropbox Scam, The Council Tax Scam, Advance-Fee Scam and The Fake QR Scam.
24. What type of phishing is whaling?
Whaling is a sophisticated type of phishing scam that targets high-level executives of a company or an organisation. Unlike regular phishing attacks, whaling involves creating a personalised email that is designed to look like it’s coming from a trusted source, such as a CEO or a senior manager.
25. Spear phishing is what type of attack?
Spear phishing is a more sophisticated type of attack, unlike regular phishing attacks that involve extensive research on the intended victim to create a believable story that would increase the likelihood of success.
It involves a targeted attack on individuals or organisations through highly personalised and convincing email messages, designed to trick recipients into giving away sensitive information or downloading malware onto their system.
26. What is a common indicator of a phishing attempt quizlet?
One common indicator of a phishing attempt quizlet is an urgent or threatening message. Phishers often use scare tactics to urge individuals to take immediate action.
For example, they may claim your account has been compromised and encourage you to enter your login credentials or personal information on a fake website.
27. What is computer phishing?
Computer phishing is a type of cybercrime where scammers send fraudulent messages to steal sensitive data, such as passwords, credit card information, and Social Security numbers.
These messages may appear to be from a legitimate source, such as a bank or government agency, but they often contain links to fake login pages or malware-infected attachments.
28. What is a phish alert?
A phish alert is a notification sent out to users by a web service or browser extension when a potential phishing attack is detected.
29. What is a phish email?
A phish email is a fraudulent message that appears to be from a reputable source, such as a bank or an e-commerce site, designed to trick people into handing over their personal and financial information.
The email typically contains a link that leads to a fake website, and once the victim enters their sensitive information, it is captured by the scammer for their gain.
30. What is a phishing call?
Simply put, a phishing call is an attempt by scammers to obtain sensitive information, such as credit card numbers, passwords, or social security numbers, by posing as a legitimate company or organisation.
These calls can be incredibly convincing and may even use intimidation tactics to coerce victims into giving up their data.
31. What is a phishing campaign?
A phishing campaign is a type of cyber attack that aims to trick individuals into divulging sensitive information by deceptive communications.
Attackers typically send emails, text messages, or voice messages that appear to be from a legitimate source, such as a trustworthy company or organisation.
They then prompt the recipient to click on a link, download an attachment, or enter personal information on a website.
Once the victim has complied with the request, the attacker may use the stolen information to commit identity theft, steal financial assets, or gain access to sensitive corporate data.
32. What is an example of a phishing email?
An example of a phishing email is an email that might lead you to a fake webpage that requires you to enter your login credentials or encourage you to click on an attachment that contains a virus.
33. What is a phishing message?
In simple terms, a phishing message is a fraudulent attempt to obtain sensitive information such as login credentials and financial details by pretending to be a trustworthy entity via electronic communication.
Common ways in which these kinds of messages are delivered include email, social media, text messages, etc.
34. What is a phishing scheme?
In simple terms, a phishing scheme is a type of online scam where criminals disguise themselves as legitimate entities, usually via email, to acquire sensitive information from unsuspecting victims. This can include personal information, credit card details, login credentials, and more.
35. What is a phishing simulation?
Phishing simulation is a process where employees receive fake emails or messages that mimic the content of real emails or messages from malicious sources.
36. What is a phishing site?
Put simply, a phishing site is a fraudulent website designed to trick people into giving away sensitive information such as usernames, passwords, and financial data. These sites often look like legitimate websites, often impersonating popular companies or institutions, and so can be difficult to spot.
37. What is a phishing test?
A phishing test is a simulation designed to test how likely individuals are to fall for a phishing scam. A phishing test involves sending out fake emails or messages to employees to see if they can identify and report the phishing attempt.
38. What is a phishing text?
Phishing text is a fraudulent text message that is sent by scammers who are looking to steal your personal information. These messages may claim to be from a bank or other trusted organisation, but they are designed to trick you into giving away sensitive information.
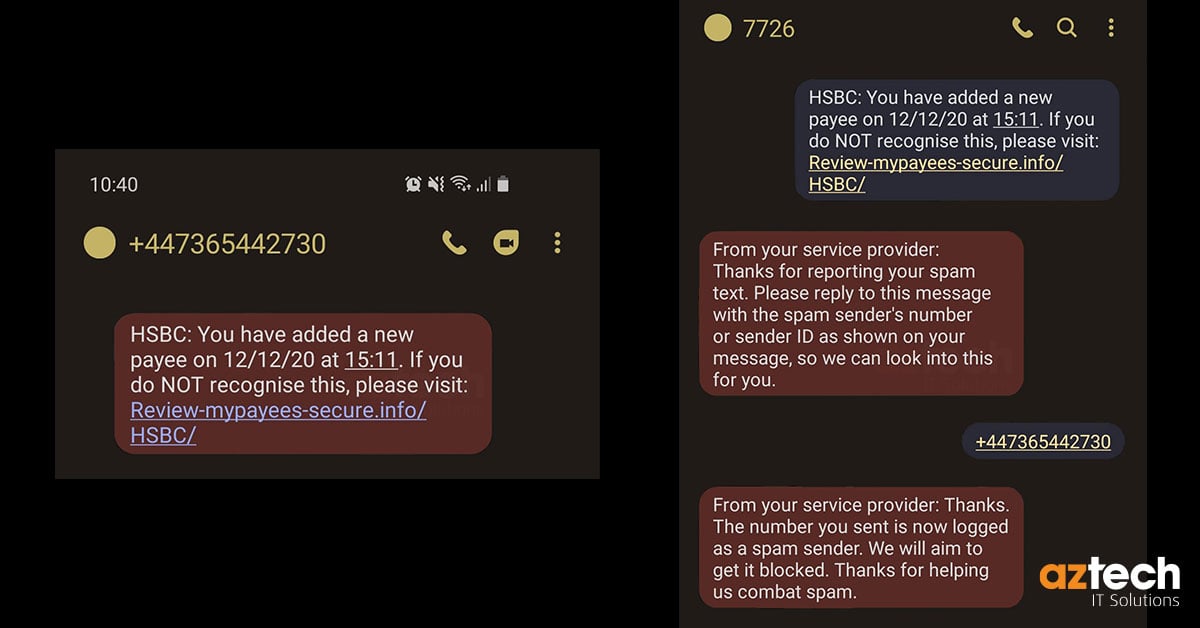
39. What is a phishing URL?
A phishing URL is a web address that is designed to look like a legitimate site but redirects the user to a fraudulent one. These types of URLs are used in phishing attacks to steal personal and sensitive information such as usernames, passwords, and credit card details.
40. What is account phishing?
Account phishing is a scam where a malicious actor tries to trick you into giving up your sensitive login information, such as your username and password.
This is typically done through fraudulent emails or messages that may seem legitimate but are designed to deceive you into handing over your personal data.
When hackers gain access to your account, they can wreak havoc on your life, from stealing your identity to draining your bank account.
41. What is an anti-phishing code?
An anti-phishing code is a security measure that helps protect individuals and businesses against phishing attempts. Essentially, it's a secret code that is unique to each user and is used to confirm the authenticity of messages from a trusted source.
By using an anti-phishing code, you can ensure that only genuine messages from trusted sources are acted upon while phishing scams can be quickly identified and discarded.
42. What is barrel phishing?
In simple words, barrel phishing is a cyber criminal tactic which involves targeting a large number of individuals at once, often through a single email blast, with the hopes of getting at least some of them to take the bait. Once an unsuspecting victim falls prey to the phisher’s tactics, sensitive information such as login credentials or financial details become compromised.
43. What is BEC phishing?
BEC phishing, or Business Email Compromise phishing is a form of cybercrime in which cybercriminals use social engineering tactics to impersonate employees, vendors, or executives to trick the target into transferring funds or providing sensitive information.
44. What is CEO fraud phishing?
CEO fraud phishing is a type of online scam that hackers use to steal money from businesses. These scams usually start with an email that appears to come from a high-ranking executive in a company, such as the CEO, CFO, or COO. The email often looks legitimate and may contain sensitive information about the company or a request to transfer funds.
46. What is clone phishing in cyber security?
Simply put, clone phishing is a sophisticated form of phishing scam where cyber criminals create a fake login page or website that appears to be legitimate, often mimicking the design and layout of the real website. They then trick unsuspecting users into disclosing sensitive information such as login credentials, credit card details, or personal data.
47. What is credential phishing?
In short, credential phishing is a type of scam where a hacker poses as a trusted source to trick victims into providing sensitive information such as passwords or banking details. This can be done through email, social media, or even fake websites.
48. What is data phishing?
Data phishing refers to the act of stealing sensitive information, such as banking or social media login credentials, by using fraudulent emails or messages that appear legitimate.
The goal of a data phisher is to trick the recipient into sharing their personal information, which can then be used for malicious purposes such as identity theft.
49. What is deceptive phishing?
Deceptive phishing is a malicious practice which involves crafting a fake website or sending a fraudulent email that appears to be trustworthy and legitimate in order to trick users into giving away sensitive information, such as passwords or credit card numbers.
Common tactics used in deceptive phishing include creating visually similar copies of legitimate websites, using social engineering to convince users to click on malicious links, and trying to create a sense of urgency or fear to pressure users into acting quickly.
50. What is the difference between spam and phishing?
The difference between spam and phishing is spam is unsolicited bulk messages that are sent to multiple recipients. It could be commercial advertising, chain letters, or malicious content sent by a third party.
On the other hand, phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details. Phishing messages often appear legitimate and urge the recipient to take immediate action.
51. What is executive phishing in cyber security?
Executive phishing is a scam where cybercriminals impersonate high-ranking executives to gain access to valuable data or funds. This form of phishing can be highly effective due to the perceived legitimacy of the sender's authority.
53. What is fly phishing?
Fly phishing is a type of online scam where criminals try to trick individuals into giving away sensitive information such as login credentials or financial data.
54. What is https phishing?
HTTPS phishing is an online scam where cybercriminals create fake websites that appear trustworthy and even display the padlock icon in the address bar.
What is Instagram phishing?
Instagram phishing is a type of scam which involves creating fake websites or login pages that look exactly like the real Instagram page, prompting users to input their login credentials.
55. What is internet phishing?
Internet phishing is a type of online scam that aims to trick users into revealing their personal or sensitive information such as passwords, credit card details, and social security numbers.
This is typically done through emails, text messages, or phone calls from a seemingly trustworthy source, such as a bank or a government agency.
56. What is password phishing?
Password phishing refers to the act of fraudulently obtaining an individual's login information by posing as a trustworthy entity, such as a legitimate website or business. This can be done through email, text, or even social media.
57. How can phishing be prevented?
Phishing can be prevented by first, being vigilant. Don't click on any links or open any attachments from untrusted sources. Check the sender's email address and look for any grammatical errors or suspicious content.
Second, use security software that can identify and block phishing attempts. Additionally, make sure your software and operating systems are always up to date, as they often contain vital security updates.
Finally, educate yourself on the latest phishing trends and how to spot a fake email or website.
59. What is phishing cybercrime?
Phishing is a type of online scam where cybercriminals send deceptive emails, text messages, or phone calls, trying to trick people into revealing their personal information, like login credentials, credit card details, or social security numbers.
60. What is phishing hacking?
Phishing hacking is a type of online scam that aims to steal sensitive personal or financial information by tricking people into giving it away voluntarily.
Phishing attacks can take various forms, ranging from fake emails and websites to social media messages and phone calls.
61. What is phishing in Outlook?
In Outlook, phishing often takes the form of an email or message that appears to come from a trusted company or individual but is actually a hoax.
63. Why is phishing dangerous?
Phishing is dangerous because of the information that can be gathered from it. This data can either be used immediately to gain access to your accounts, without your knowledge.
If a cybercriminal has access to your passwords, they can easily gain entry into your accounts as it'll appear as if the actual user is logging in, (which is why you should set up Multi-Factor Authentication as it is another barrier to help protect your data).
In addition to this, your data could be harvested and sold onto other sites such as the Dark Web where multiple cybercriminals can purchase the information for as little as £2.
How can Aztech IT help?
We are experienced Managed Security Service Professionals, we can provide you with User Awareness Training, including fake phishing to test your users and see how they would react to these types of threats. In addition, we can scan the Dark Web to see if any of your credentials are already for sale to cybercriminals.
Or if you'd prefer to find out how well your organisation is currently protected, why not begin with an IT Security Audit? Our Security Audit will analyse your network, finding any weaknesses or areas of concern so you'll know exactly where you need to focus your security strategy.
If you'd like to find out more about our services, please get in touch by calling us on 03300949420, or contact us with our online chat.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)