Should you be wary of QR codes (quick response code) in your emails and text messages? While QR codes are a great way to access information quickly and easily, they are also being used by threat actors in a phishing scam.
Quishing is the combination of 'QR code' and 'phishing' and is used for QR code-based fraud which uses phishing campaigns to target users and businesses alike.
In this blog post, we’ll explore what QR phishing attacks are and will provide guidance on best practices for precautionary measures you can take to protect yourself from falling prey to these QR code scams.
Let’s dive in!
What is Quishing and How Does It Work?
In simple terms, Quishing is a form of phishing attack which involves the manipulation of users through malicious QR codes.
Quishing is a term that has been coined from the words QR code phishing to describe this attack and are interchangeable.
In a quishing attack, threat actors employ this technique on large scale to redirect users to a fraudulent website that either download malware or gain sensitive information like login information or payment information.
Now, let us look how exactly does quishing work:
Firstly, scammers will send you an email or text message asking you to scan the QR code. These phishing emails and texts will include an urgent request such as limited time special offer or urgent payment required as shown on below images.
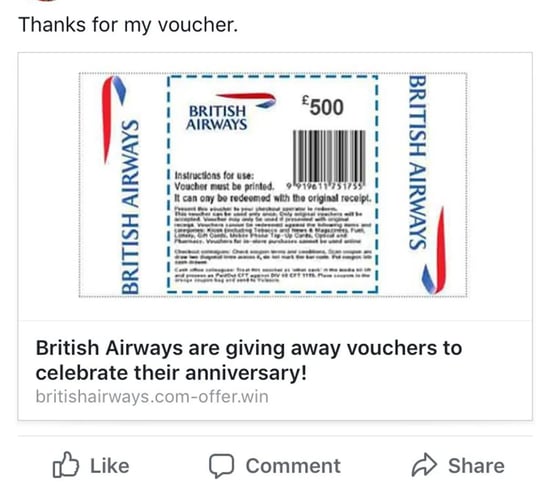
This is a trick called QR phishing which creates a sense of urgency for the unsuspecting victims so that the QR codes are scanned ASAP.
Once users scan the QR codes, the QR code takes you to a legitimate looking website where you can be asked to add your personal or banking account information for offers. This website could then automatically start downloading malicious software, spyware etc onto your mobile device.
If you do this, threat actors try to steal data including login information, credit card information and personal details or infect your device with malicious software for any malicious purposes.
To make it more clear for you, here is an example video of how the quishing attack looks like:
Email security vendors have recently discovered a quishing campaign utilising QR codes to bypass security gateways.
These gateways typically scan text for URLs, but the scammers aimed to steal users' Microsoft login credentials.
Example of Quishing
An example of quishing attack is where threat actor sends you an email with a malicious QR code, asking you to secure your Facebook account. It creates a sense of urgency to click these malicious links.
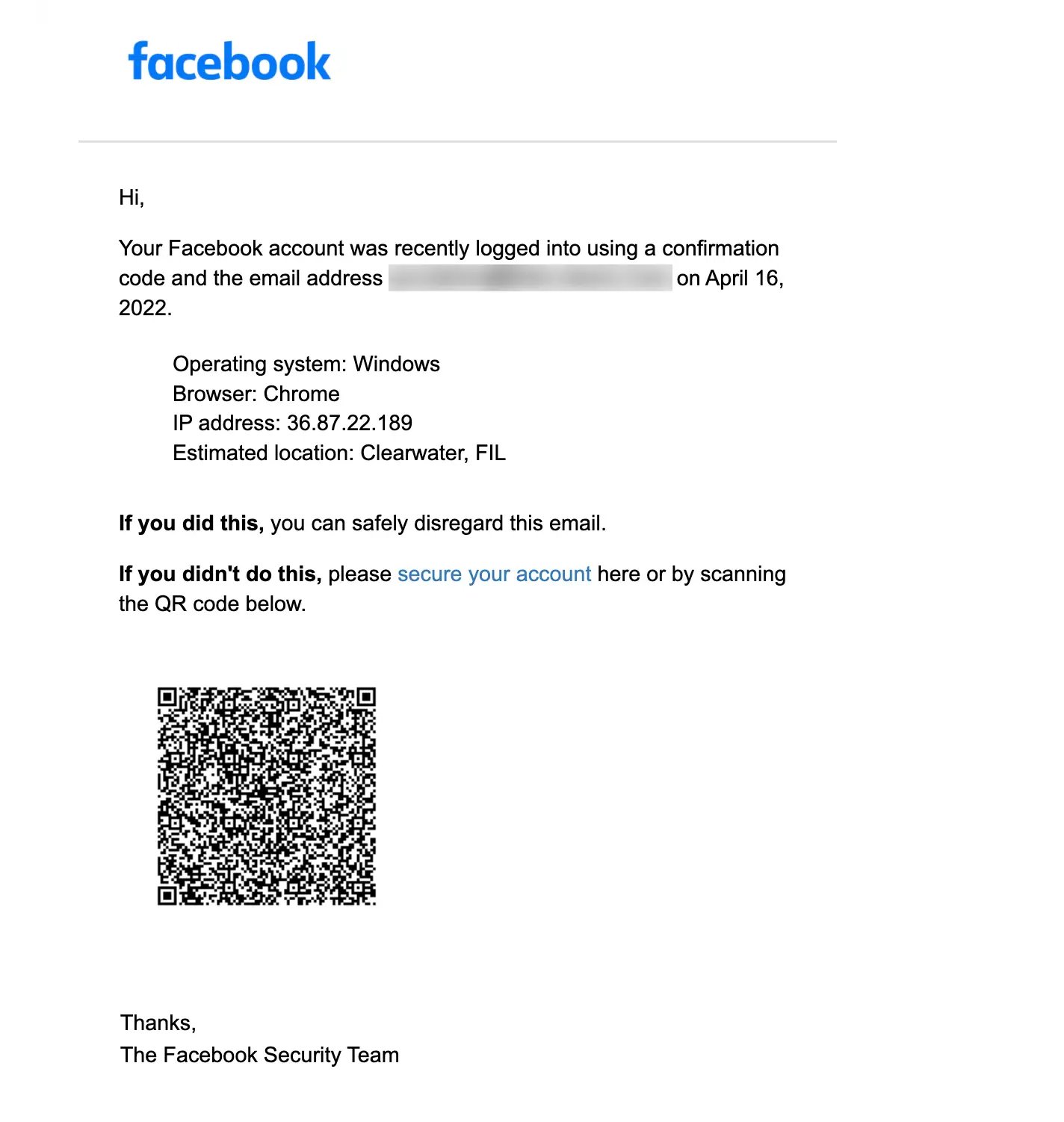
For any scam emails, forward them to report@phishing.gov.uk, and for scam text messages, forward them to 7726 for free.
Moving ahead, let us get into how to spot the signs of a quishing attack when you receive any suspicious emails or messages.
Signs to Identify Quishing Attack
Here are 5 tips to spot a quishing attack:
Sense of urgency: If you receive any emails or texts stating any kind of request to scan a QR code urgently such as ‘limited time offer’, ‘your account is hacked’ and ‘urgent payment required’ (tv licencing fraud payment) it is possible a scam.
Unfamiliar sender: One of the most common signs of a QR code phishing emails is an unfamiliar sender. If you receive an email from someone you don’t recognise, it’s best to be extremely wary before you scan any QR codes or downloading any PDF attachments.
Suspicious URL Link: Another sign of a QR code phishing email is suspicious URL. Scammers often use shortened URL links to hide their true destination.
Poor grammar: Scammers often use poor grammar and spelling in their emails, as they may not have a good grasp of the language or are trying to rush through writing the message.
Requests for personal information: A credible company will never ask for your personal information via scanning a QR code through emails.
How to Avoid Quishing Attacks?
Here are 6 best practices to avoid and prevent a quishing attack:
1. Check the source and URL
If you are being redirected to a website, check the URL including the HTTPS. If the URL doesn’t match what you are trying to access, then it can be a sign of a fraudulent website.
Always make sure that the URL uses a HTTPS connection.
Additionally, most browsers will display a green lock icon next to the URL if it is using an HTTPS connection.
2. Always check the email quality
Before scanning a QR code in an email or actioning anything the email is asking of you, it’s best practice to really check the quality of the email.
For example, you can check the email address that it has been sent from and will easily be able to tell if it isn’t a legitimate source.
You can also check the quality of the QR code, poor grammar and spelling errors are signs of a Quishing emails.
3. Use a QR Code scan App
One of the safest ways to scan any QR code is to use a QR scanner App.
See our blog 9 Tips To Spot a Fake QR Code Scam which shares the top 5 free QR Code Scanner Apps Android & iOS.
4. Always use multifactor authentication
Two factor authentication requires users to provide two pieces of information in order to gain access to their accounts. This could include a combination of a username and password, or a QR code sent via text message or mail.
By using 2FA, users can ensure that even if their credentials are compromised, the scammer will still not be able to access their accounts without the second piece of information.
5. Never share your personal information
Quishing often involve asking for personal information like mobile phone number which also leads to SIM swap scam.
Also, if you are asked for any type of financial information when accessing a website via QR code, it is likely a phishing scam and should be avoided.
6. Report any suspicious activity
If you suspect that you have encountered a QR code phishing attack, be sure to report it immediately so that other users can be warned about the potential danger.
You can report suspicious activity by contacting your local law enforcement agency or filing an online complaint with organisations such as the Federal Trade Commission or Internet Crime Complaint Center (IC3).
Final Takeaway
In conclusion, users should always stay alert with email phishing scam which ask you to offer something by scanning a malicious QR codes.
Also, you should always check any malicious URLs and pdf attachments before clicking any link.
Always remember the signs of QR phishing, such as a sense of urgency, emails from unfamiliar senders, suspicious URL, poor grammar in the email body and requests of any personal information.
You can help protect yourself by using QR code scanner apps before scanning from mobile device, always checking the URL source and email quality, never sharing any personal information and if you suspect something suspicious don't hesitate to report it away.
Finally, if you have been targeted by a QR phishing scam, simply change your passwords, contact your bank, and always disconnect from Wi-Fi.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)





.jpg?width=536&name=Blog%20Hero%20Banners%20(2).jpg)
