Whether you're a savvy user looking to learn more about cybersecurity best practices or a business considering transitioning its operations to the cloud, understanding the potential cloud security risks will help keep your data protected against malicious actors.
In this blog post we'll look at the trending security risks of cloud computing in 2024 and help you understand how best to protect your business from these cloud security risks and challenges when moving data to the cloud.
18 Trending Cloud Security Risks of 2024

Here are the latest cloud security threats of 2024 to watch out for:
1. Data Breaches
Data breaches are one of the most common cloud security risks associated with its storage. The breach occurs when an unauthorised user gains access to sensitive information stored in the cloud.
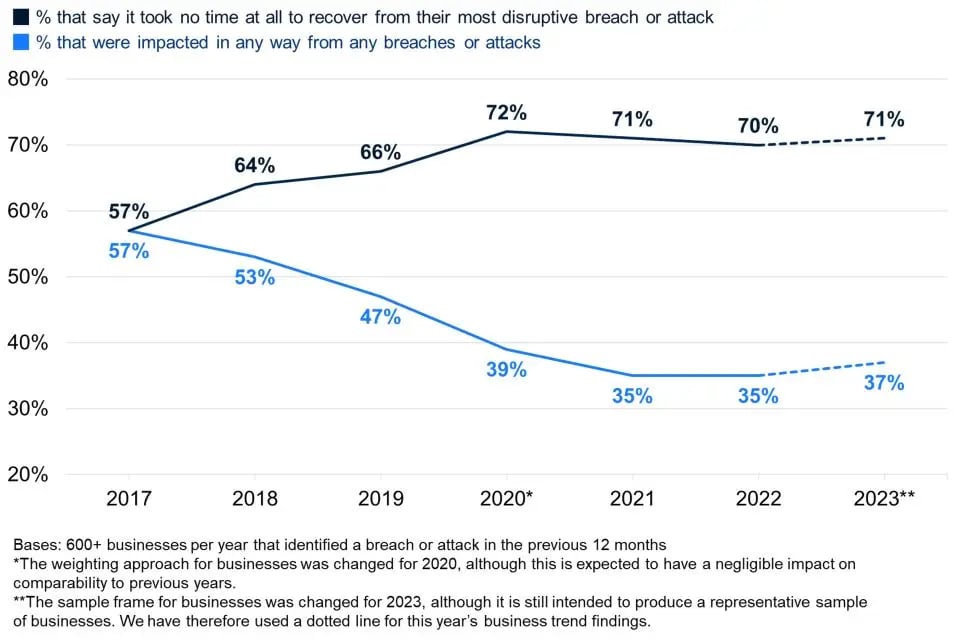
The cloud security threats in 2024 due to data breach can be increased if the cloud service provider does not have adequate security measures such as encryption and authentication protocols.
To understand the tactics of data breach prevention, read our blog on 'How to Prevent Data Breaches'.
2. Unauthorised Access
Another security risk of cloud computing is unauthorised access. This means that someone who does not have permission to access your data can gain access to it, either through a malicious attack or by exploiting vulnerabilities in the system.
To prevent these security risks of cloud computing, businesses must use strong authentication methods and regularly audit their systems for any potential cloud security risks.
3. Phishing Attacks
Phishing attacks is another trending security risk of cloud computing associated with storage systems today.
These attacks involve sending emails containing malicious links or attachments which appear legitimate but actually contain malware designed to steal user credentials or other sensitive information once opened by unsuspecting users.
QR scams, also known as fake QR codes, quishing or QR code phishing and SIM swapping attacks, are currently trending in 2024.
In 2024, a financial advisory company called Kroll encountered a cloud security threat involving a malicious actor using the SIM swapping technique.
This incident serves as a recent example of cloud security issues.
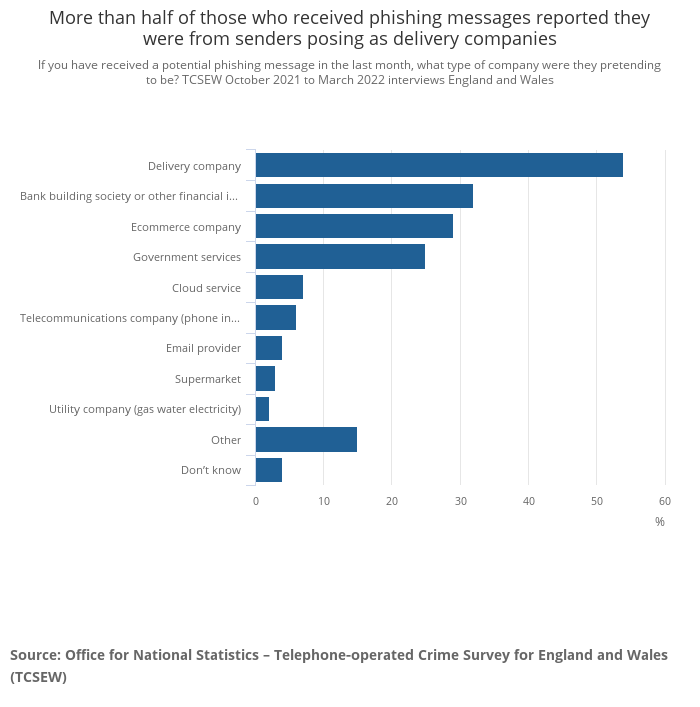
To protect from these cloud security risks, businesses should educate employees about phishing scams and implement technologies such as anti-phishing software and QR code scanner apps on all devices connected to their cloud storage system in order to protect against these types of attacks.
4. Denial-of-Service (DoS) Attacks
Denial-of-service (DoS) attacks are another major cloud computing security risk which is trending in 2024. These attacks involve flooding a network with requests until it becomes overwhelmed and unable to process legitimate requests from users.
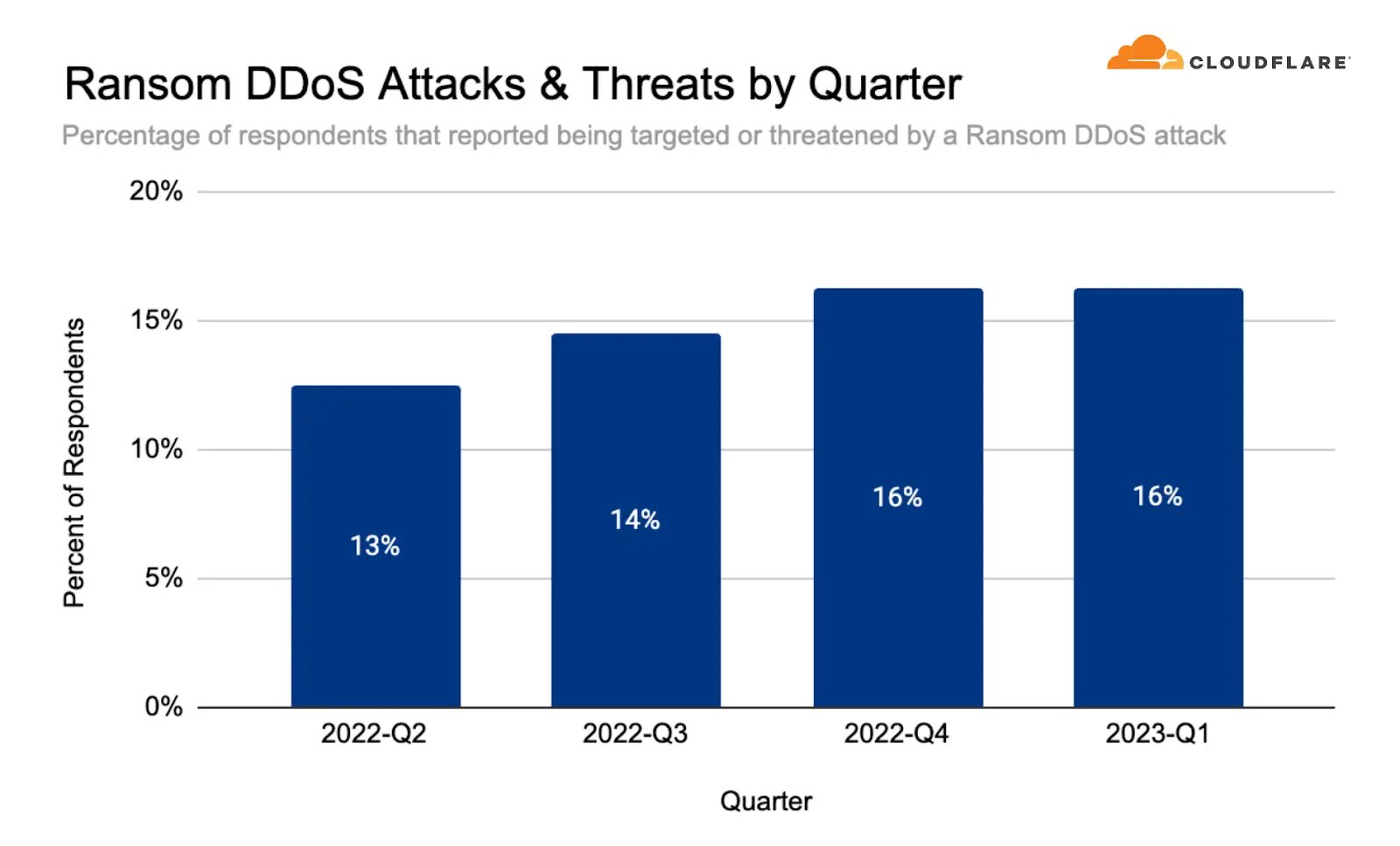
DoS attacks can cause significant disruptions for organisations that rely on their network for business operations, resulting in lost productivity, revenue, and customer trust.
To prevent these security risks of cloud computing, businesses should use firewalls and intrusion detection systems that are capable of detecting suspicious activity on their networks.
5. Data Loss
Data loss is another serious cloud storage security risk. If a user accidentally deletes important files, or if there is an issue with the cloud provider’s servers, then all of the stored data could be lost forever.
To combat this cloud security risk, businesses should have a cloud data backup in place to ensure that their data is always available and protected from accidental deletion or corruption.
6. Insufficient Encryption
Insufficient encryption can also lead to cloud security issues with its storage. If the data is not properly encrypted, it can be accessed by any unauthorised user without permission.
To help prevent these cloud security risks, businesses should make sure that they are using strong encryption algorithms and are regularly auditing their systems for any potential vulnerabilities related to encryption.
7. Malware Attacks
Malware attacks are another common cloud computing cyber security issue. Malware can be used to infect devices and networks with viruses, spyware, ransomware, and other malicious programs designed to steal sensitive information or disrupt operations.
To protect from these cloud security threats, businesses should ensure that they have adequate malware protection software installed on all devices connected to their cloud storage system.
8. Insecure APIs
Insecure application programming interfaces (APIs) can also be a security risk of cloud computing as they may contain vulnerabilities that can be exploited by malicious actors.
To protect from these cloud security threats, organisations should ensure that all APIs used within their system are secure, and regularly audit them for any potential issues related to security or privacy concerns.
9. Unpatched Software
Unpatched software can also present a cloud security risk as attackers may be able to exploit known vulnerabilities in outdated software versions in order to gain access to sensitive data stored on the system.
To prevent from these cloud security threats, businesses should ensure that all software used within their system is up-to-date and patched regularly in order to reduce the risk of attack from malicious actors.
10. Weak Passwords
Weak passwords are another major cloud security risk associated with cloud storage systems. If users choose weak passwords, attackers can easily guess them and gain unauthorised access.
In order to prevent from this type of cloud security issue, businesses should require users to create strong passwords consisting of at least 8 characters including upper-case letters, numbers, symbols, etc.
Additionally, they should also encourage users to change passwords regularly and use two-factor authentication whenever possible.
11. Account Hijacking
Account hijacking is another trending cloud security threat in 2024 as attackers are able to gain access to accounts by exploiting weak passwords or social engineering techniques such as phishing emails. These also go by names such as SIMJacking or SIM hijacking.
To prevent these kind of cloud security challenges, organisations should deploy multi-factor authentication solutions such as two-factor authentication which requires users to enter both a username and password, along with an additional code sent via text message or email, before being granted access.
12. Social Engineering Attacks
Social engineering attacks are also one of the trending cloud security risks as it refers to attempts by attackers to manipulate individuals into divulging confidential information through deception techniques such as phishing emails, phone calls impersonating IT support staff, etc.
To protect against these cloud security threats, organisations should educate employees about potential threats they may face online, as well as implement strict password policies requiring strong passwords are used for all accounts connected the company’s network.
13. Lack of Visibility
Lack of visibility into who has access, what type of data is being accessed, and how long it has been accessed can also pose significant cloud security risks when using cloud storage systems.
To prevent, businesses should ensure that they have adequate visibility into their system so that they can detect suspicious activity quickly and take appropriate action if necessary.
14. Data Leakage
Data leakage is also one of the biggest cloud security threats. It occurs when confidential information stored on a system is unintentionally exposed due to inadequate security measures or malicious attacks.
To prevent these cloud security issues, organisations should employ proper data handling practices such as encryption and regular audits of their systems for any potential vulnerabilities related to data leakage.
15. Insider Threats
Insider threats are also one of the trending cloud computing security issues and challenges. It refers to individuals inside an organisation who have legitimate access but misuse it for personal gain or other malicious purposes such as stealing confidential information.
To protect against these cloud security risks, organisations must implement strict policies regarding user permissions and monitor user activity closely for any suspicious behaviour which could indicate insider threat activity taking place on the system.
16. Unsecured Connections
Unsecured connections between devices used within a business network can also lead to significant risks associated with cloud storage security as attackers may be able intercept unencrypted traffic traveling across these connections in order to steal confidential information stored on the system.
Businesses must ensure that all connections between devices used within their network are secured properly at all times in order to protect against these cloud security risks from occurring.
17. Poor Configuration
Poor configuration settings on devices used within a business’s network can also lead to serious risks associated with cloud storage security as attackers may be able to exploit misconfigured settings in order to gain access to confidential information stored on the system without permission.
Businesses must ensure that all devices used within their network are configured correctly at all times in order to reduce the cloud storage security risks from malicious actors.
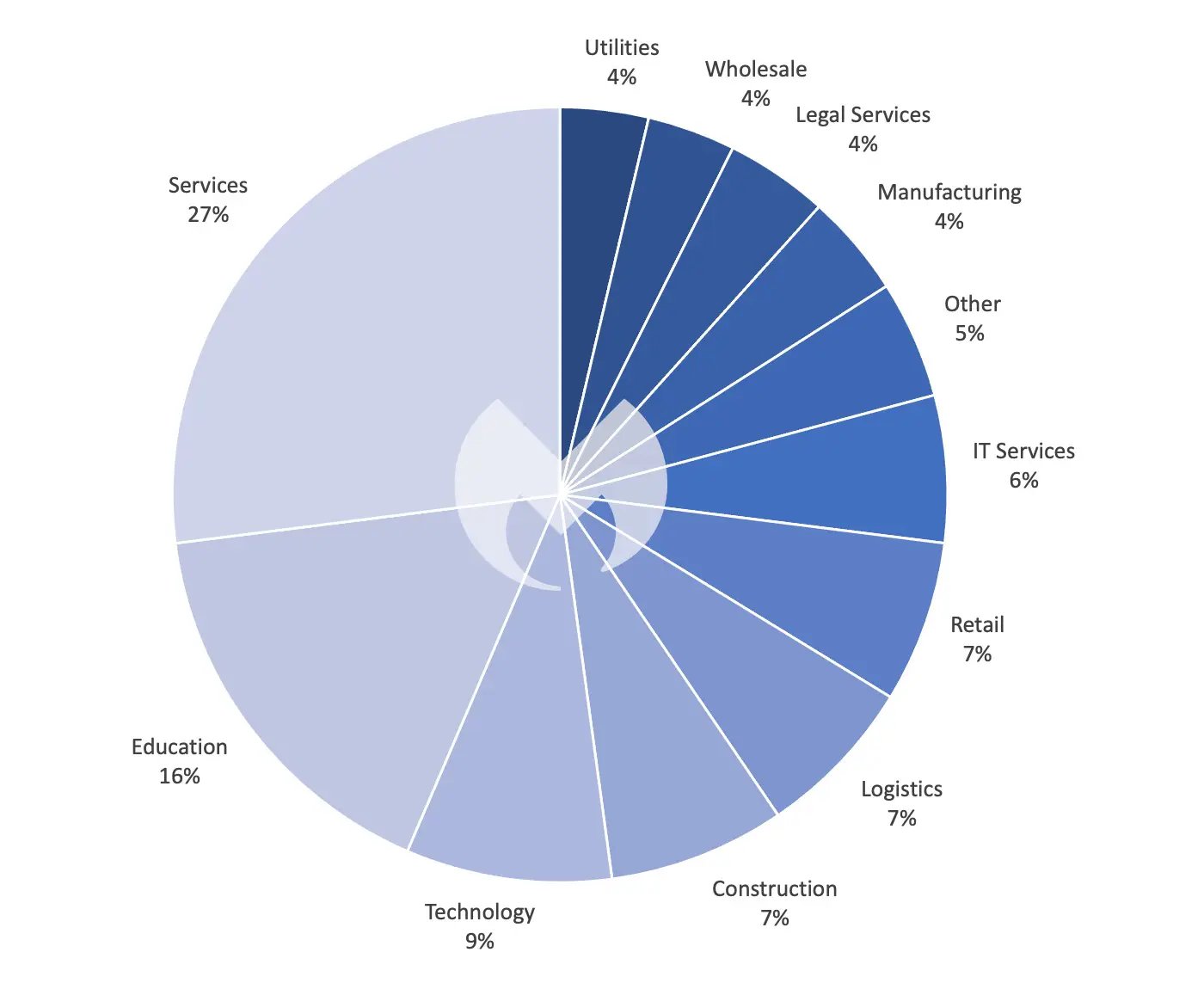
18. Server Vulnerabilities
Server vulnerabilities refer to weaknesses present within servers hosting clouds services which attackers exploit to gain access to confidential information stored within them.
Common server vulnerabilities include outdated software versions, lack of patching, unencrypted communications, insecure file permissions etc.
To prevent these cloud storage security risks, businesses must regularly scan servers to detect, identify, and fix, if any.
How to Prevent Cloud Security Risks
Here are 8 ways to prevent cloud storage security risks and safety concerns for any business:
1. Conduct A Cloud Security Risk Assessment
The first step in protecting cloud storage safety concerns is by conducting a cloud security risk assessment.
Cloud security risk assessments are an essential process to ensure the safety of data stored in the cloud.
There are potential cloud security threats that can target your business, such as cyber-attacks, unauthorised access, data breaches, and insider threats.
Therefore, it's essential to conduct a thorough cloud security risk assessment to identify potential vulnerabilities and to design appropriate strategies to prevent cloud computing cyber security issues.
With the help of cloud security experts, you can evaluate your cloud environment and develop a robust security plan that meets your unique business needs.
2. Use of Strong Passwords
The next step to preventing cloud storage security risks is to use strong passwords.
A strong password should be at least 12 characters long and contain a mix of upper and lowercase letters, numbers, and special characters.
Additionally, it is important to avoid using the same password for multiple accounts as this increases the risk of your data being compromised if one account is hacked.
It is also important to change your passwords frequently in order to ensure that they remain secure.
3. Enable Two-Factor Authentication
Another way to help prevent cloud storage security risks is to enable two-factor authentication (2FA).
2FA requires users to enter an additional code after entering their username and password in order to access their account.
Also, this code can be sent via text message or generated by an authenticator app on a user’s phone or other device.
Enabling 2FA adds an extra layer of protection against hackers who may try to gain access to your data.
4. Use Encryption Methods
Encryption is another way to help protect your data stored in the cloud from unauthorised access and prevent from cloud computing cyber security risks.
Encryption scrambles data so that it cannot be read unless the person has the encryption key, which only you should have access to.
Most cloud storage providers offer some form of encryption, so make sure you take advantage of this feature when storing sensitive information in the cloud.
5. Monitor Access Logs
Monitoring access logs can also help you detect any suspicious activity on your cloud storage account and act quickly if necessary.
Most cloud storage providers provide detailed logs that show who has accessed certain files and when they were accessed.
So, make sure you check these regularly for any unusual activity that could indicate a potential breach or attack on your system.
6. Limit Access Rights
Limiting access rights can also help reduce the security risks of cloud computing as it restricts who can see certain files within your cloud storage account and prevents unauthorised users from accessing them without permission.
You should also set up different levels of permissions for different users depending on their role within the business in order to ensure that only those with appropriate clearance are able to view sensitive data stored in the cloud.
7. Keep Your Software Updated
Ensuring that all software utilised to access or manage your cloud storage stays up to date is crucial in mitigating cloud computing security risks.
In addition, regular updates often incorporate essential security patches that safeguard against emerging threats and vulnerabilities identified since the previous update was released.
Make sure you keep all software up to date with the latest version available from the provider in order to ensure that you are protected against any potential threats or attacks targeting your system.
8. Use Reputable Service Providers
Finally, to prevent security risks of cloud computing, it is important to choose reputable service providers when selecting a provider for storing data in the cloud.
Reputable service providers will have robust security measures in place, such as encryption, two-factor authentication, and regular monitoring.
These will help reduce cloud computing security risks.
Make sure you do thorough research before selecting a provider so that you know they are reliable and trustworthy enough for storing sensitive data securely.
Cloud Security Risks FAQs
What are the security risks for cloud computing?
In 2024, trending cloud computing security risks and challenges includes QR phishing attacks, account hijacking, insider threats, data breaches, DOS attacks, malware attacks etc.
What are the 5 most common security issues relating to cloud computing?
The five most common security issues relating to cloud computing are insecure APIs, insufficient encryption, data loss, server vulnerabilities and poor configuration.
Why is cloud storage risky?
Cloud storage is risky due to the cybersecurity threats, such as data breaches, account hacking attempts, insider threats and data leakage.
What are 3 disadvantages of cloud storage?
The 3 disadvantages of cloud storage are security, unsecured connections, and server vulnerabilities.
What are the 5 security issues relating to cloud computing?
The five security issues related to cloud computing are data breaches, data loss, account hijacking, insider threats, and lack of visibility.
What are the risks of cloud storage?
The risk of cloud storage for example, storing sensitive information on the cloud might make it vulnerable to hacking and data breaches. Furthermore, some cloud storage providers have access to your files, which raises concerns about privacy and ownership.
What is the most alarming concern of cloud computing?
The most alarming concern of cloud computing is its cybersecurity.
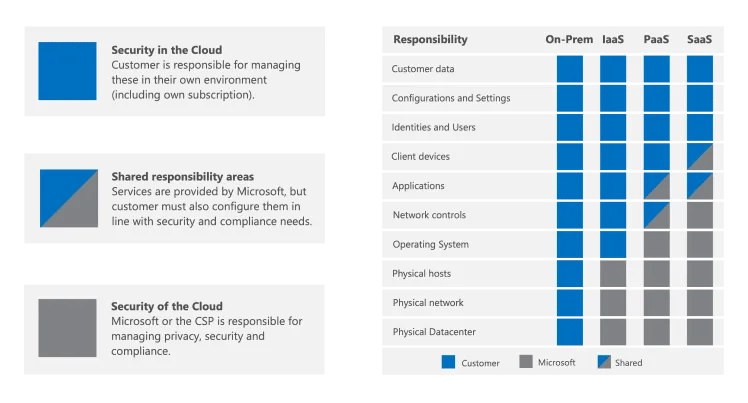
How Safe is Cloud Storage for my Business?
If you take the necessary precautions of its security, cloud storage is a secure way to store your business data. You can protect your data by implementing encryption, using multi-factor authentication, and choosing a reputable cloud storage provider.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)







