Are you looking for more information about security audits? If so, you've come to the right place!
This blog post will provide a comprehensive overview of all the different types of security audits that are available.
From vulnerability assessments to penetration testing, each audit is designed with unique goals in mind and requires its own once-over when it comes time to review your organisation's cyber security services.
We'll look at exactly what these types of audits entail and discuss why they're necessary for any cyber security professional.
So, if you're ready to learn more about the various ways an audit can help keep your business secure, then let's get started!
A cybersecurity audit is a systematic and fully comprehensive review and analysis of your company’s information technologies infrastructure, which highlights any weaknesses or opportunities cybercriminals have of penetrating your systems.
There are four core cybersecurity audits any business should conduct regularly:
- Compliance Audit
- Vulnerability Assessment
- Penetration Test
- Risk Assessment
Firstly let us understand, what a security audit is and why it is important for your business.
What is a security audit?
In today's world, security online is important like never before. Hackers and cybercriminals are constantly looking for vulnerabilities to exploit.
One of the best ways to protect yourself and your business is through a security audit. But what is a security audit?
In simple words, security audit is a thorough examination of your computer systems and networks to find vulnerabilities, identify potential threats, and assess your overall level of security.
Why is it important to conduct a security audit?
A security audit can help you pinpoint weaknesses in your security measures and provide a roadmap to improve your overall security posture.
So, if you're serious about protecting your assets and data, a business IT security audit is a critical first step.
Internal Security Audits
Internal security audits are a crucial element of any organisation's security protocols.
These audits serve as a preventative measure against potential breaches in network security, allowing organisations to identify and address any weaknesses in their systems before outside threats have a chance to exploit them.
There are several types of security audits that an organisation can conduct, including network security audits, application security audits, and data security audits.
Each type of audit focuses on different aspects of a company's security measures, ensuring that all potential vulnerabilities are thoroughly evaluated.
By conducting these audits regularly, organisations can maintain a robust security framework that protects sensitive data and information from falling into the wrong hands.
External Security Audits
External security audits involve an independent organisation reviewing your company's security measures to identify vulnerabilities that may be exploited by attackers.
Additionally, this helps organisations protect sensitive information, prevent financial losses, and preserve their reputation.
There are several types of security audits, including network penetration testing, vulnerability assessments, and compliance audits.
Network penetration testing simulates a cyberattack to identify weaknesses in your security system. Vulnerability assessments identify vulnerabilities in software, systems, and hardware.
Compliance audits ensure an organisation meets specific regulatory requirements. Conducting an external security audit helps businesses stay ahead of potential security threats and maintain the confidentiality, integrity, and availability of their data.
What is the difference between internal and external security audits?
Here are the key differences between an internal security audit and an external security audit in terms of scope, frequency, cost and reports.
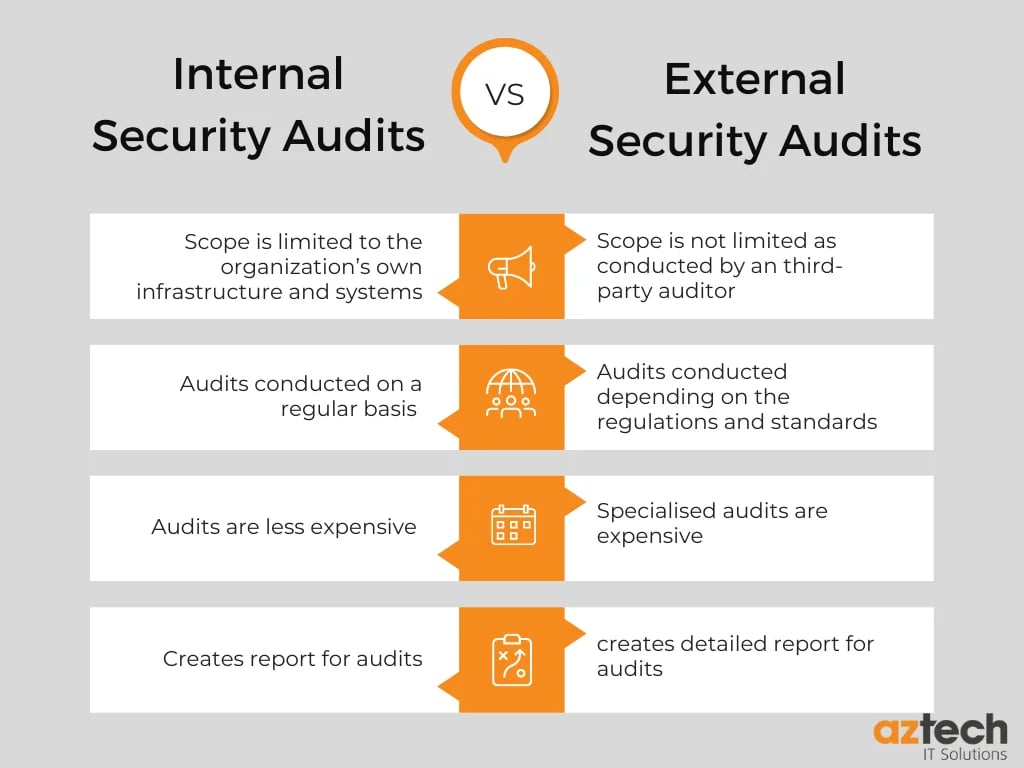
1. Scope
The scope of an internal security audit is generally limited to the organisation’s own infrastructure and systems.
An external security audit, on the other hand, is conducted by an independent third-party auditor who evaluates the organisation’s compliance with industry standards and regulations.
The scope of an external security audit may include evaluating the organisation’s network architecture, physical access controls, data encryption practices, user authentication procedures, and other areas related to information security.
2. Frequency
Internal security audits are typically conducted regularly (e.g., annually, or biennially) to ensure that the organisation’s information assets remain secure over time.
External security audits may be conducted more frequently depending on the specific regulations or standards that apply to the organisation (e.g., financial institutions may be subject to external audits every year).
3. Cost
Internal security audits are generally less expensive than external audits since they do not require the services of a third-party auditor.
However, external auditors often possess specialised knowledge and experience which can be beneficial in identifying potential risks or vulnerabilities that may not be apparent during an internal audit process.
4. Reports
Internal and external security audits both result in reports which detail any areas where improvements can be made to better protect an organisation’s information assets from unauthorised access or misuse.
The reports generated by both types of audits should provide recommendations for improving existing policies and procedures as well as suggestions for implementing new ones where necessary.
Types of Security Audits
Here are the five types of security audits your business should conduct.
1. Compliance Audit
A compliance audit is an independent evaluation of an organisation’s security policies and procedures to determine if they are following applicable laws, regulations, and industry standards.
During these types of security audits, the auditor will review the organisation’s security policies and procedures to ensure that they are adequate and up to date.
The auditor may also evaluate the organisation’s physical security measures, such as access control systems and CCTV cameras.
Compliance audits are necessary for businesses such as retail, finance, healthcare, or government which must comply with certain regulations.
These types of security audits are to show that a company meets the laws required to conduct business safely in their industry.
Without compliance audits, your company can be susceptible to fines which can lead to clients leaving to work with fully compliant companies.
Compliance audits for cybersecurity will examine if regulations are being followed, access controls and company policies.
2. Vulnerability Assessment
A vulnerability assessment is an evaluation of an organisation’s IT infrastructure to identify weaknesses that could be exploited by malicious actors.
During a vulnerability assessment type of security audit, the auditor will scan the organisation’s networks for known vulnerabilities and then recommend remediation steps to address any issues that are identified.
Vulnerability testing can be conducted by your IT team or an external expert who will test various systems to see if they are in danger of causing a security breach.
In addition, these types of security audits can include running specific software to test for vulnerabilities, accessing the network from a remote network and testing from inside of the network.
3. Penetration Test
A penetration test is a simulated attack on an organisation’s IT infrastructure to determine if it can be breached by malicious actors.
During a penetration test type of security audit, the auditor will attempt to gain unauthorised access to the organisation’s systems using various techniques such as social engineering or exploiting known vulnerabilities.
The goal of a penetration test is not only to identify weaknesses in the system but also to provide recommendations on how these weaknesses can be addressed.
You can conduct internal and external penetration testing. Internal penetration testing focuses on internal systems, whereas external will focus on areas that are publicly exposed such as email systems or WIFI.
To maximise the benefits of penetration testing a hybrid of both should be conducted.
4. Security Architecture Review
A security architecture review is an evaluation of an organisation’s security architecture to determine if it meets best practices for securing data and other assets from malicious actors.
During a security architecture review type of security audit, the auditor will examine all aspects of an organisation’s IT infrastructure including its network design, operating systems, applications, databases, and more.
The goal of this type of audit is to identify any potential weak points in the system that could be exploited by attackers.
5. Risk Assessment
A risk assessment is a process used to identify potential risks within an organisation's IT environment and assess their impact on business operations should they occur.
During a risk assessment type of security audit, the auditor will analyse all aspects of an organisation's IT environment including its people processes, technology components, data flows, etc, to identify any potential risks that could affect business operations should they occur.
The goal of these types of security audits is not only to identify existing risks but also to recommend strategies for reducing or eliminating them.
Performing risk assessments will help recognise and prioritise risks and help identify different types of threats that your businesses could be vulnerable to.
Following a risk assessment checklist, such as the AZTech Cybersecurity assessment checklist, will help educate companies on what they should be looking out for, as well as configure strategies on how to overcome these weaknesses.
Furthermore, for some businesses in heavily regulated industries, risk assessments can aid with compliance issues.
Security Audit-Related Frequently Asked Questions
What are the 3 types of audits?
Three types of audits exist: financial audits, operational audits, and compliance audits.
What is a financial audit?
Financial audits examine a company's financial statements to determine whether they accurately represent the financial position of the company.
What is an operational audit?
Operational audits, on the other hand, assess the efficiency and effectiveness of a company's processes and procedures.
What is a compliance audit?
Compliance audits assess whether a company is operating by legal regulations governing its activities.
What is included in the security audit?
Security audits include various aspects such as risk assessments, vulnerability testing, and compliance reviews. By conducting regular security audits, organisations can identify, address, and prioritise the critical security risks that should be addressed to safeguard their valuable data and infrastructure.
What is an internal security audit?
An internal security audit is a comprehensive process that evaluates an organisation's internal controls, policies, and procedures to identify potential threats and vulnerabilities.
What type of security control is an audit?
As a security control mechanism, a security audit provides an in-depth analysis of existing security measures, identifying vulnerabilities, and making recommendations to improve security.
These types of security audits provide insights into security risks, and liabilities, and ensure compliance with industry standards and regulations.
Why are security audits important?
Security audits are important because, by conducting regular security audits, organisations can ensure that they are adequately protecting their data, resources, and reputation from cyber-attacks and other security threats.
Moreover, security audits also help organisations to comply with legal regulations and industry standards, ultimately giving a competitive edge over others.
What is an example of a security audit?
An example of a security audit is an external audit, where a third-party organisation is hired to assess the company's security practices.
During the audit, the organisation may evaluate the effectiveness of access controls, encryption practices, and incident response procedures.
What is the role of a security audit?
The role of a security audit involves the systematic and comprehensive analysis of a company's IT infrastructure and policies to identify any vulnerabilities or weaknesses in its security systems.
This audit helps to assess the effectiveness of existing security measures and identify areas that need improvement or additional security measures.
What is a security audit checklist?
A security audit checklist is a comprehensive list of items that are required to be reviewed and evaluated to ensure that a company's security measures meet legal and regulatory standards.
It is a detailed document that assists companies in identifying potential vulnerabilities in their systems and provides a framework for conducting security audits.
How do I prepare for a security audit?
You can prepare for a security audit by familiarising yourself with security protocols and guidelines that are relevant to your business, identifying any vulnerabilities within your system by conducting a risk assessment and lastly, by making sure that you have all the necessary documentation ready for the auditor, including policies, procedures, and incident reports.
Conclusion
If you have any questions about what type of cybersecurity audit your business should conduct, or if you have any concerns about your cybersecurity, we offer a free cybersecurity assessment performed by one of our experts here at AZTech, or you can download our cybersecurity assessment checklist. View our full range of cybersecurity services.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)








