Cybercrime has steadily increased over the years due to technological advances in the digital world and as such, there are more opportunities for criminals to target businesses of all sizes with malicious activity.
As an IT Security Manager or a cyber security professional, this likely sounds overwhelming - but don't fret!
By implementing proactive measures now, you can protect your business from becoming victimised by cybercrime in 2024.
In this blog post, we’ll explore five essential cybercrime prevention tips you can take today to safeguard your business against future attacks.
Users are typically the main cause of a data breach within companies, but as CybSafe states,
‘if criminals rely on human error to facilitate most cyber attacks, then surely people also have the power to prevent most cyber attacks. People – historically seen as a weakness – can be your ultimate defence. Moving from A to B just requires a change of behaviour’
How to Prevent Cyber Crime
Here are top 5 cybercrime prevention tips for your business:
1. Multi-Factor Authentication
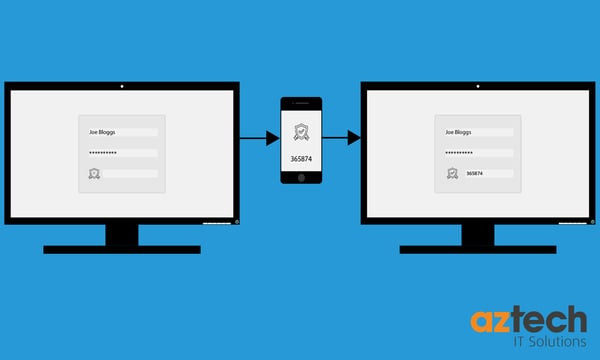
Multi-factor authentication, commonly referred to as MFA, is a powerful solution to prevent cybercrime. MFA is a security protocol that requires users to provide multiple forms of identification to access their accounts.
When logging in, MFA prompts users to supply a password and then another form of identification that's unique to them, such as a fingerprint.
This two-factor authentication greatly improves security by reducing the chances of a cyber-attack. Even if hackers obtain your password, they still cannot access your account without the second factor.
By adding layers of security, MFA makes your account far more secure and can ultimately prevent unauthorised access to your sensitive data and personal information.
With multi-factor authentication, you need to provide something you know, such as your password or pin, and something else, such as a one-time code received on your phone, generated by a token, or your fingerprint.
Without access to these additional devices, a hacker cannot gain access to your account.
Furthermore, with multi-factor authentication, you’ll be alerted if someone tries to access your account or data.
In today's world where cybercrime is prevalent, MFA is a highly recommended method for safeguarding your digital identity.
2. Update Your System and Applications

Another cybercrime prevention tip is removing outdated software. Keeping your system and applications up to date is essential; not only for a smooth and efficient workflow, but also for preventing cybercrime.
Cybercriminals are constantly on the lookout for vulnerabilities that they can exploit to gain access to your data or network. Updating your system and applications ensures that any security loopholes are patched before attackers can take advantage of them.
This includes important security updates that fix known vulnerabilities and bugs that could be exploited by cybercriminals. As such, it's imperative to keep your system and applications up to date to stay protected against evolving cyber threats. A few extra moments spent updating your software and security systems can go a long way in preventing a cyber-attack.
A perfect example of this would be the WannaCry ransomware that attacked a vulnerability in Microsoft’s operating system.
A patch for this vulnerability had been released a few months before the attack in May, but those who had not updated became open targets to the ransomware.
This is why something as simple as updating your software can be crucial in helping prevent cyber attacks.
3. Password Manager

The next important tip is to use a password manager. As our world becomes increasingly digital, protecting our personal information and online identity has never been more important. One of the most basic steps we can take to prevent cybercrime is to use a strong password for each of our accounts.
However, it can be overwhelming to manage and remember a unique password for every site we use.
This is where a password manager comes in, allowing us to securely store and easily access all our passwords in one place. Password managers also often offer additional features, such as automatic password generation and two-factor authentication.
By utilising a password manager, we can take a crucial step towards protecting our online presence and staying one step ahead of potential cybercriminals.
Your passwords should be updated every few months, with a different password being used for every application, device or service you use.
We understand that it is nearly impossible to remember a different password for every application or device, so instead of writing them down, use a password manager to protect them.
These devices can generate and store your passwords for you with strong encryption, protecting them with a master password, which allows you to focus on your work rather than what password to use next.
4. Backup Your Data
In today's technology-driven world, it has become increasingly important to protect your personal and sensitive data from the prying eyes of cybercriminals. So, the next important cybercrime prevention tip is to create a backup for your data.
Backing up your data is an essential step in safeguarding against potential data loss and theft. So, how can you ensure that your digital information stays secure?
Well, by regularly backing up your data on a secure and encrypted platform, you can mitigate the risk of losing all your crucial information in one go.
Moreover, it is crucial to create strong and complex passwords for all your online accounts and avoid opening emails or clicking on links from unknown sources.
These simple yet effective steps can go a long way in ensuring that your data remains safe from prying eyes and the threat of cybercrime.
A data breach can happen to any business, which is why it’s crucial to have a recovery plan in place.
Creating frequent backups of your data ensures your files are recoverable if your computer becomes unusable due to malware, ransomware or even theft.
Mobile devices and PCs can be configured to automatically backup to a cloud base service.
This allows you to access your data from another device if a breach or attack happens on your main computer.
Your backups should be securely encrypted to prevent cyber crime.
5. Report Any Issues to Your IT Team Immediately
In today's digital age, cyber criminals are constantly looking for ways to infiltrate and exploit vulnerable networks.
So, the final cybercrime prevention tips is to report an issue. And, it's critical to report any issues to your IT team immediately.
By quickly identifying and addressing potential problems, you can help prevent costly data breaches and protect sensitive information.
In addition to being vigilant about reporting issues, there are also steps you can take to prevent cybercrime in the first place.
These may include regularly updating passwords, avoiding clicking on suspicious links or emails, and utilising antivirus software.
By staying informed and proactive, you can help ensure the safety and security of your organisation's valuable assets.
A data breach can start from simply clicking on a link in a suspicious email, therefore if you notice any issues with your computer, report them to your IT team immediately.
Be aware of:
- A significant decrease in performance
- A sudden increase in pop up ads/spam
- A new homepage or default search engine
- Frequent error messages
- Antivirus alerts about malware/viruses being present
How Can AZTech help?
AZTech offer a continued service using a multi-layered IT security solution, which gives you the assurance that your cybersecurity is being managed proactively, and appropriately.
Furthermore, a significant data loss could be catastrophic for your business; we can help by implementing a Disaster Recovery Plan to protect your mission-critical systems and data.
Get in touch to find out more and protect your business today.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)