Do you know what penetration testing or pen testing is, and why it's important for your business?
Penetration testing, also known as pen testing, is a technique used for gaining access to the security of an IT system by attempting to breach some or all of its security measures using the same tools and techniques as a potential attacker.
Moreover, it is important to note that a penetration test should be considered a supplementary method for gaining assurance in your organisation's vulnerability assessment and management processes, rather than a primary method to identify vulnerabilities.
It involves simulated attacks by ethical hackers or pen testers to gain access to the target device's security posture. By mimicking the tactics of real-world attackers, pen testing helps businesses identify and address potential weaknesses before they can be exploited.
In this comprehensive guide, we will get into the world of pen tests, exploring their importance, process, types, pros and cons, and some of the best practices to conduct penetration testing.
What is Penetration Testing?
Penetration testing, also known as pen testing or ethical hacking, is a proactive approach to identifying critical security vulnerabilities within the security features of an application, system or network infrastructure.
Penetration tests involve conducting a simulated attack by ethical hackers or penetration testers to gain access to the target systems' security posture.
The primary goal of conducting this simulated attack is to gain access to security controls that are effective and to identify any vulnerabilities in the computer system before they are exploited by malicious actors.
In addition to using ethical hacking methods, ethical hackers may also use social engineering attacks to find vulnerabilities in the computer system.
For example, they may send phishing emails to company employees or even pose as delivery people to gain physical access to the building.
Why is it Crucial to Conduct a Penetration Test?
Without a doubt, conducting penetration tests is a critical step in ensuring the security of your computer system.
Here are five compelling reasons why you should not ignore this vital cyber security measure:
1. Identifying Security Vulnerabilities: Penetration tests help identify security weaknesses and vulnerabilities in computer systems, networks, and applications and gain access to them before attackers exploit them.
2. Risk Assessment: By uncovering vulnerabilities, pen testing enables organisations to assess the potential risks associated with their systems and prioritise remediation efforts accordingly.
3. Maintaining Compliance: Many regulatory standards and frameworks, such as PCI DSS (Payment Card Industry Data Security Standard), mandate regular penetration testing as part of security compliance requirements.
4. Enhancing Security Measures: Penetration testing provides valuable insights into the effectiveness of existing security measures and helps strengthen an organisation's overall security posture.
5. Preventing Data Breaches: By proactively identifying and addressing security flaws, pen testing helps mitigate the risk of data breaches and safeguard sensitive data.
3 Types of Penetration Testing
There are mainly three types of penetration testing which include external, internal and web application penetration tests.
1. External Test
The testing team simulates attacks outside the organisation's network perimeter in an external pen test. This type of testing assesses the security of external-facing computer systems, such as web servers, session management, remote access tools, email servers, and firewalls.
2. Internal Test
Internal pen testing involves assessing the security of computer systems and networks from within the organisation's internal network. The internal test aims to identify security vulnerabilities that may be exploited by insiders or unauthorised network intruders.
3. Web Application Test
Web application pen tests target web-based software flaws, to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws. It helps in securing web applications against common cyber security threats.
The Penetration Testing Process
The penetration testing process is a systematic approach to assessing the security posture of a target system or network. It involves a series of steps aimed at identifying vulnerabilities, exploiting them, and providing recommendations for remediation.
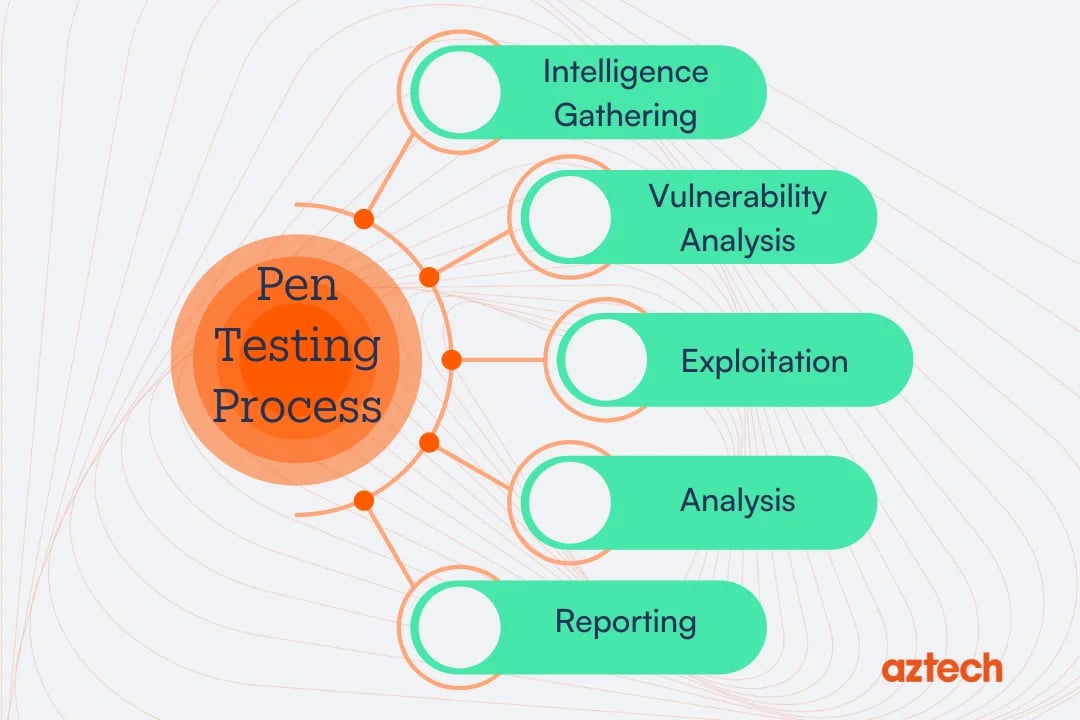
Let's delve into each phase of the pen testing process in detail:
1. Pre-Engagement
This initial phase involves defining the scope, objectives, and rules of engagement for the penetration test.
The scope outlines the specific computer systems, applications, and network segments that will be tested, while the objectives define what the testing team aims to achieve.
Rules of engagement establish boundaries for the testing, such as prohibited actions or limitations. Effective pre-engagement ensures that the penetration test aligns with organisational goals, resources, and constraints.
2. Intelligence Gathering
Intelligence gathering is also known as reconnaissance in which the pen testers collect information about the target system or network such as operating system, services and resources used by the security team.
Pen testers utilise various techniques, such as open-source intelligence (OSINT), network scanning, and social engineering, to gather information about the target's infrastructure, architecture, and potential vulnerabilities.
Intelligence gathering helps pen testers identify potential entry points and prioritise areas for further investigation during the testing process.
3. Vulnerability Analysis
In this discovery phase, the pen testers analyse the information gathered during reconnaissance to identify known vulnerabilities and weaknesses in the target system.
So, the pen testers conduct pen tests such as vulnerability scans, analyse network traffic, and review system configurations to identify potential security flaws.
Vulnerability analysis helps pen testers prioritise vulnerabilities based on their severity and potential impact on the business.
4. Exploitation
Once vulnerabilities are identified, pen testers attempt to exploit them to gain unauthorised access to the target system.
This phase involves using various exploitation techniques, such as SQL injection, buffer overflow, or brute-force attacks, to bypass security controls and gain entry into the target environment.
Successful exploitation of these pen tests demonstrates the severity of identified vulnerabilities and their potential impact on the business operation.
5. Post-Exploitation
After gaining initial access to the target system, pen testers aim to maintain persistence within the environment to assess the system's defences and potential avenues for further exploitation.
This pen tests phase involves techniques such as privilege escalation, backdoor installation, and covert communication channels to evade detection and maintain access over an extended period.
By maintaining access, pen testers can simulate real-world attack scenarios and assess the effectiveness of security controls in detecting and responding to intrusions.
6. Analysis
Once the pen testing is complete, the penetration testing team analyses the findings to evaluate the overall security posture of the target system.
These pen tests involve reviewing the vulnerabilities identified during the pen test, assessing their severity and potential impact on the business, and prioritising them for remediation.
The analysis phase provides valuable insights into the effectiveness of existing security measures and informs decision-making regarding risk mitigation strategies.
7. Reporting
The final phase of the penetration testing process involves documenting the findings and recommendations in a comprehensive report.
The report typically includes an executive summary highlighting key findings and recommendations, detailed technical findings outlining identified vulnerabilities and exploitation techniques, and remediation strategies for addressing identified security flaws.
A well-written report provides stakeholders with actionable insights to improve the organisation's security posture and mitigate potential risks.
What are the Pros and Cons of Pen Testing?
Pros of Penetration Testing
-
Identifies Security Weaknesses: Helps in uncovering vulnerabilities and security flaws before they can be exploited by attackers.
-
Risk Mitigation: Enables organisations to assess and mitigate potential security risks proactively.
-
Compliance Requirements: Helps in meeting regulatory compliance requirements by conducting regular security assessments.
-
Enhances Security Awareness: Raises awareness among security teams and stakeholders about potential threats and vulnerabilities.
Cons of Penetration Testing
-
Costly and Time-Consuming: Penetration testing can be expensive and time-consuming, especially for large and complex systems.
-
False Positives: There is a risk of false positives, where vulnerabilities may be incorrectly identified or reported.
-
Disruption to Operations: Penetration testing activities may cause disruptions to normal business operations if not planned and executed carefully.
-
Limited Scope: Penetration testing may not uncover all possible security vulnerabilities or threats, especially if the scope of testing is limited.
What Should Good Penetration Testing Include?
A comprehensive assessment of an organisation's attack surface is a crucial part of a successful penetration testing engagement.
A good pen test should include thorough planning, comprehensive testing, the use of diverse techniques, risk assessments, detailed reporting and collaboration with stakeholders.
Let's explore each of these components in detail:
1. Thorough Planning
Effective planning is essential for the success of a penetration testing engagement. This includes defining clear objectives, scope, and rules of engagement for the test.
The scope outlines the specific systems, applications, and network segments that will be tested, while the objectives define what the testing team aims to achieve.
Rules of engagement establish boundaries for the testing, such as prohibited actions or limitations.
Additionally, planning involves coordinating with stakeholders, obtaining necessary approvals, and allocating resources to support the testing effort.
2. Comprehensive Testing
A good penetration test exercise should include testing of both external and internal systems, including web applications, networks, and mobile devices.
External testing focuses on assessing the security of systems accessible from the internet, such as web servers and email servers.
Internal testing evaluates the security of systems and networks within the organisation's internal network, including employee workstations and internal servers.
Also, pen testing should include an assessment of wireless networks, cloud-based services, and other relevant components of the organisation's IT environment.
3. Use of Diverse Techniques
Pen testers should employ a variety of techniques, tools, and methodologies to identify security vulnerabilities. This includes both automated scanning tools and manual testing techniques.
Automated tools can help identify common vulnerabilities quickly and efficiently, while manual testing allows testers to conduct in-depth analysis and identify more complex vulnerabilities that tools may miss.
Additionally, testers may utilise social engineering techniques to assess the effectiveness of employee security awareness and training programs.
4. Risk Assessments
Not all vulnerabilities pose the same level of risk to an organisation. A good penetration testing exercise should prioritise identified vulnerabilities based on their severity and potential impact on the organisation.
This involves assessing the likelihood of exploitation and the potential consequences of a successful attack.
Vulnerabilities that pose the greatest risk to the organisation's assets, operations, or reputation should be addressed with the highest priority.
5. Detailed Reporting
The findings of the penetration testing exercise should be documented in a comprehensive report.
The report should include an executive summary highlighting key findings and recommendations for senior management, as well as detailed technical findings outlining identified vulnerabilities and exploitation techniques for IT and security teams.
Each vulnerability should be described in detail, including its severity, potential impact, and recommended remediation steps.
The report should also include actionable recommendations for addressing identified security weaknesses and mitigating potential risks.
6. Collaboration with Stakeholders
Effective communication and collaboration with stakeholders are critical throughout the pen testing process.
This includes working closely with the security testing team to understand the organisation's infrastructure and security controls, coordinating security testing activities to minimise disruption to business operations, and providing timely updates on testing progress and findings.
Collaboration with stakeholders ensures that the penetration test aligns with organisational goals and that vulnerability identification is addressed promptly.
Manual vs Automated Penetration Testing
Both manual and automated penetration testing have their advantages and limitations:
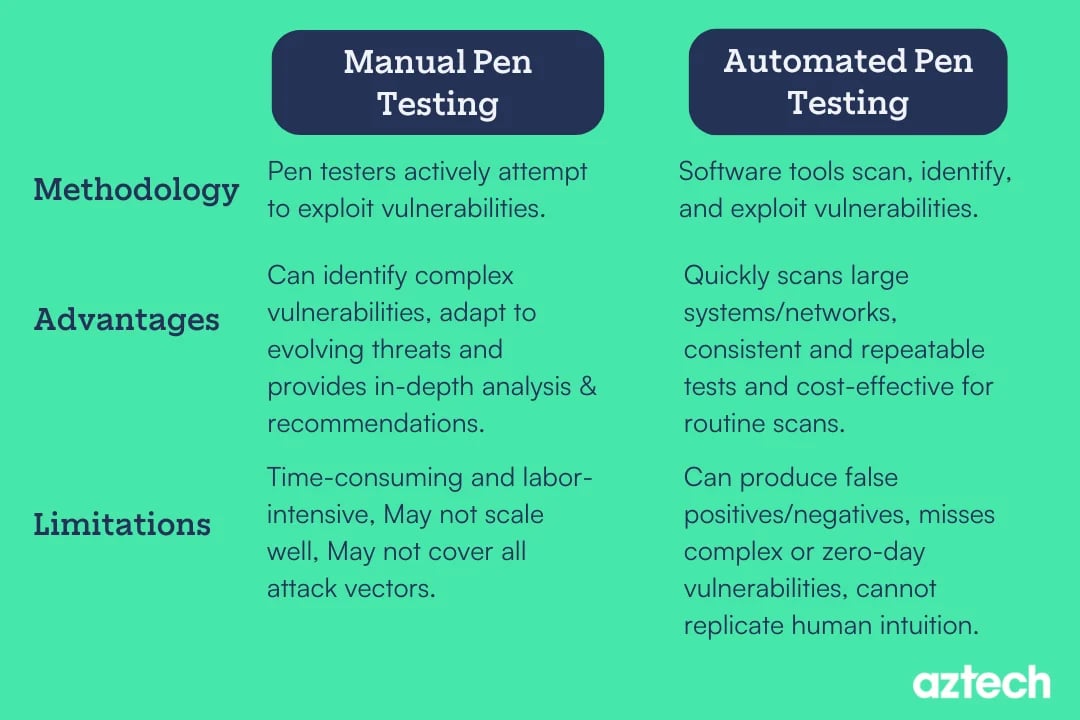
Manual Penetration Testing
-
Advantages:
-
Allows for deeper analysis and identification of complex vulnerabilities.
-
Provides a more thorough understanding of the target system's security posture.
-
Can uncover vulnerabilities that an automated tool misses.
-
-
Limitations:
-
Time-consuming and labour-intensive.
-
It may be prone to human error and bias.
-
Requires skilled and experienced penetration testers.
-
Automated Penetration Testing
-
Advantages:
-
Rapid and efficient scanning of large networks and systems.
-
Can identify common vulnerabilities quickly.
-
Provides consistent and repeatable results.
-
-
Limitations:
-
Limited in detecting complex or unknown vulnerabilities.
-
It may generate false positives or false negatives.
-
It cannot replace the expertise and intuition of human pen testers.
-
Best Pen Testing Tools
Several penetration testing tools are available, catering to various aspects of security testing.
Some of the best pen testing tools as per our experts include:
-
Metasploit: A popular framework for developing, testing, and executing exploits against target systems.
-
Nmap: A powerful network scanning tool used for discovering hosts and services on a network.
-
Burp Suite: A comprehensive web application security testing tool used for scanning, crawling, and exploiting web applications.
-
OWASP ZAP: An open-source web application security scanner for finding vulnerabilities in web applications.
-
Wireshark: A network protocol analyser that captures and displays data packets in real-time.
-
SQLMap: An automated SQL injection and database takeover tool.
-
Nessus: A vulnerability scanner that identifies security vulnerabilities, configuration issues, and malware in systems and networks.
Why Choose Aztech For Your Penetration Testing Services?
If you choose Aztech as your penetration testing service provider, you can enjoy numerous benefits and assurances that are vital for protecting your digital assets and maintaining strong cybersecurity measures within your organisation. Aztech is a standout player in the world of penetration testing for several reasons.
Aztech's penetration testing comprises skilled and certified professionals who conduct penetration tests across different industries and environments. They identify vulnerabilities in networks, applications, and systems and use advanced methodologies to simulate real-world cyber threats.
Aztech provides customised penetration testing services for various industries, including finance, legal, education, government agencies, manufacturing, and construction companies. Their approach is tailored to meet the unique needs and regulatory compliance standards of each client.
At Aztech, our pen testing service uses cutting-edge tools and techniques to conduct thorough security assessments. We leave no stone unturned in identifying exploitable vulnerabilities in your organisation's security posture.
In addition to technical expertise, our security professionals prioritise clear communication and transparency throughout the pen test process. They provide detailed reports that not only outline discovered cyber security issues but also offer actionable recommendations for remediation. This enables your business to proactively address security gaps, secure software and systems and strengthen its defences against cyber threats.
Aztech's commitment to excellence extends beyond the initial engagement, as we offer ongoing support and guidance to help clients continuously improve their cyber security posture.
Whether you require application security solutions or additional testing following system updates or assistance with implementing recommended security tests, Aztech remains a trusted partner dedicated to your organisation's long-term security assessment.
Conclusion
In conclusion, the pen test plays a critical role in assessing and enhancing the security posture of your business by identifying and mitigating potential security vulnerabilities and weaknesses.
By simulating real-world attacks, penetration testing services provide valuable insights into the effectiveness of security measures and help organisations stay one step ahead of cyber threats.
Whether conducted manually or using automated tools, penetration testing should be integral to any organisation's cyber security strategy to safeguard against evolving threats and protect sensitive data from unauthorised access.
If you are looking for excellent penetration testing services in London and across the UK, Aztech can assist you. Please don't hesitate to reach out to us.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)







