Are you curious about what goes on behind the scenes of effective cyber security operations?
Have you heard the term "Cyber Security Operations Centre" (CSOC) thrown around, but aren't sure what it means or how it could help your organisation?
As a cyber security professional, understanding exactly what is involved in running and maintaining a CSOC can help save time and money down the road.
In this blog post, we'll take an in-depth look at some of the key elements of CSOCs to help give you better insight into how they work within an organisation's larger security structure.
86% of UK cybersecurity professionals said that they experienced an increase in attempted and successful attacks due to more employees working remotely.
The rapid and unplanned rise in remote and hybrid workers have left many organisations with blind spots and a lack of visibility of vulnerable points in their IT security.
Without full visibility of your IT systems, you are faced with questions such as:
- How would you know if a bad actor logged into your email from an unauthorised computer?
- How would you know if a server was under attack or already breached?
- How would you know if a personally owned computer was attacking the network from the inside?
What is a Cyber Security Operations Centre (CSOC)?
The Cyber Security Operations Centre (CSOC) is the hub of an organisation's security posture. It is a central location where security teams monitor and defend against cyber attacks 24/7.
The CSOC leverages advanced technology and skilled analysts to detect, investigate, and respond to potential threats based on real-time data.
It is important to note that the CSOC is not just for larger organisations, but serves to defend all sizes of organisations against cyber threats.
Purpose of CSOC
The purpose of CSOC is to improve an organisation's security posture by employing proactive and reactive measures to protect critical assets.
With the constant evolution of cyber threats, a CSOC is essential for any organisation to be properly prepared and antifragile against these ever-growing cybersecurity challenges.
The purpose of a SOC (Security Operations Centre) or also known as a Cyber Security Operations Centre (CSOC) is to monitor, prevent and detect, investigate, and respond to cyber threats 24/7/365 by using a combination of specific processes and technology solutions.
Additionally, different types of Cyber Security Operation Centre (CSOC) will monitor and analyse activity on servers, endpoints, networks, databases, applications, websites, and other systems searching for suspicious or anomalous activity and behaviour.
The CSOC is then responsible for recording and reporting any potential security threats and further investigating the said threat.
The CSOC houses a cybersecurity team that is responsible for monitoring and protecting all business assets including brand integrity, personnel data, business systems, and intellectual property as well as overseeing all cybersecurity strategy and implementation.
What does a Cyber Security Operations Centre (CSOC do?
1. Prevention and Detection
The SOC monitors and protects, Endpoints, Users, Cloud Services, Applications and On-Premises Networks, 24/7 and uses a combination of processes and technology to detect potential harmful threats, which ensures that any malicious behaviour can be blocked, preventing any damage before it is caused.
2. Investigation
All possible malicious activities are investigated further, so the SOC can identify the nature of the threat, and how far it had already penetrated the IT infrastructure.
A security analyst, usually a member of the SOC team, will perform tests on the network and security from a perspective of a hacker to identify any weaknesses so they can be amended before they are exploited.
3. Response
Once the investigation is completed, the SOC team will then create a response to the issue, this can include performing tasks such as terminating potentially harmful processes and isolating endpoints.
The SOC team is also responsible for restarting all systems once the attack has been appropriately and fully dealt with. This can include wiping and resorting endpoints, recovering any lost or compromised files and reconfiguring systems.
How to Manage your Cyber Security Operation Centre
1. Keeping your SOC in-house
If you have the capabilities of housing an effective SOC in-house, then there are many benefits of keeping your IT security in-house.
In addition, keeping your SOC in-house means that your business has full control over all security measures, incidents, and monitoring.
Additionally, you can tailor all security operations to best suit the business’s needs.
Factors to include if you are considering an in-house SOC:
- Do you have an in-house team, or the ability to recruit an in-house dedicated SOC team?
- Do you have the facilities and team to ensure your IT security is being monitored 24/7/365
- Do you have an IT budget that will support the procurement of the tools needed for the SOC? E.g., Hardware and software or if a virtual SOC Cloud infrastructure.
2. Outsourcing your SOC
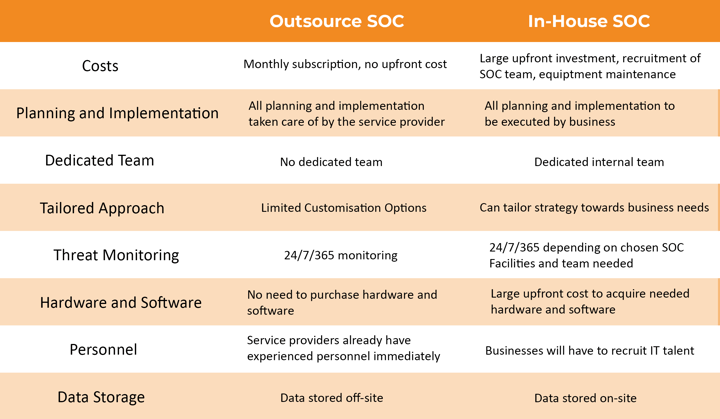 The above table shows the major difference between outsourced SOC and in-house SOC
The above table shows the major difference between outsourced SOC and in-house SOCThere are many benefits to partnering with an outsourced SOC provider, as previously mentioned in the ‘types of SOC’ section. When partnering with a SOC provider there is no large upfront investment, as most MSP’s bill their services on a monthly subscription basis. Furthermore, you will not have to recruit specialist IT talent to build, run and manage your SOC.
Secondly, you will have access to cybersecurity skills immediately. This is beneficial for understanding what you need to set up your SOC framework, running and monitoring your SOC and having expert advice when and if there is a cyberattack.
Moreover, having access to SOC experts will make implementation and scaling easy and simple.
Conclusion
If you have any questions or concerns about your cybersecurity, we offer a free cybersecurity assessment performed by one of our experts here at AZTech, or you can download our cybersecurity assessment checklist. View our full range of cybersecurity services.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)



.png)


