As a cyber security professional or medical doctor, keeping up with the latest advancements in cyber security is essential to meeting the needs of your patients and clients. With this in mind, you may be curious as to what changes are projected for 2023 so that you can stay ahead of the curve when it comes to best practices. In this blog post, we'll be exploring upcoming changes related to cyber essentials that every cybersecurity practitioner should know about. From new data protection requirements to revolutionary encryption strategies, these updates will make sure all important digital assets remain secure and compliant at all times. Read on for a comprehensive look into how these changes will impact you!
The Cyber Essentials scheme, approved by the Government, is designed to safeguard organisations of all sizes against common cyber attacks. It consists of five technical controls that effectively protect against these threats.
By obtaining the Cyber Essentials certification badge, organisations demonstrate to their customers, investors, and suppliers that they have implemented the minimum level of government-approved cyber security measures, instilling trust and confidence in the safety of their data and business operations.
To stay ahead of the ever-evolving threat landscape, a dedicated team of experts consistently reviews and enhances the Cyber Essentials scheme. This ensures that UK businesses can proactively raise the bar in safeguarding their cyber security.
Cyber Essentials Changes 2023 - Latest Update
The NCSC has released an updated set of requirements (version 3.1) for the Cyber Essentials scheme, effective from 24th April 2023.
This exciting update introduces the new 'Montpellier' question set, replacing the previous 'Evendine' set.
It's important to note that any ongoing assessments initiated prior to 24th April will still follow the requirements of version 3.0 with the Evendine question set.
This includes all assessment accounts created before the aforementioned date. Be sure to stay informed and take advantage of these changes to enhance your cybersecurity practices!
Changes to the scheme this year are as follows:
1. Updated definition of 'software' to clarify inclusion of firmware
Software now encompasses operating systems, commercial off-the-shelf applications, plugins, interpreters, scripts, libraries, network software, and firewall and router firmware.
Why was the change made?
Firewall and router firmware serve as the operating systems for these devices. As firewalls and routers play a crucial role in security, it is vital to ensure their operating systems are up to date for optimum security measures.
Device listing: All applicants must provide details of their laptops, desktops, servers, computers, tablets, and mobile phones, including the make and operating system.
Firewalls and routers: For these devices, applicants only need to list the make and model; no specific firmware version is required.
By asking for the make and model on firewalls and routers, the Assessor can determine if the devices are still receiving security updates to the firmware. This ensures overall security and protection.
2. Asset management is a crucial aspect of Cyber Essentials.
While it may not be a specific control, it is a paramount security function recommended for all.
By incorporating asset management into the Cyber Essentials requirements, the significance of maintaining good asset management practices is emphasised.
Why was the change made?
Asset management goes beyond simply creating lists or databases that collect dust. It involves establishing and maintaining accurate information about your assets to facilitate day-to-day operations and informed decision-making.
Cybersecurity experts often refer to asset management as a fundamental cyber hygiene practice that aids in meeting all five controls of Cyber Essentials. Neglecting proper asset management can lead to major security incidents when active assets go unnoticed.
Implementing effective asset management helps businesses track and control devices as they are introduced into the network.
So, remember, keeping track of your assets is not only a security best practice but also an essential component of Cyber Essentials.
3. BYOD guidance
Bring Your Own Device (BYOD) is the practice where employees use their own personal devices for work purposes. Essentially, it means that you get to use your own smartphone, tablet, or laptop for work-related tasks.
Here's how it works: an organisation maintains control over all the company data and resources that you access or store on your device.
However, it's important to note that the device itself remains your property.
BYOD offers flexibility and convenience, as it allows you to seamlessly integrate your personal and professional lives.
Plus, it can save you the hassle of carrying around multiple devices. So, if you've ever wondered if you can use your beloved personal device for work, the answer is yes—with BYOD, it's totally possible!
Detailed information about BYOD can be found on NCSC's BYOD guidance.
4. Clarifying the inclusion of third-party devices
To ensure a comprehensive assessment, it is important to consider all end user devices owned by your organisation, as well as those loaned to third parties. We have included a new table to provide clear guidance on this matter.
For devices that are not owned by your organisation, the table below will help you understand what is included in the assessment scope and what is not.
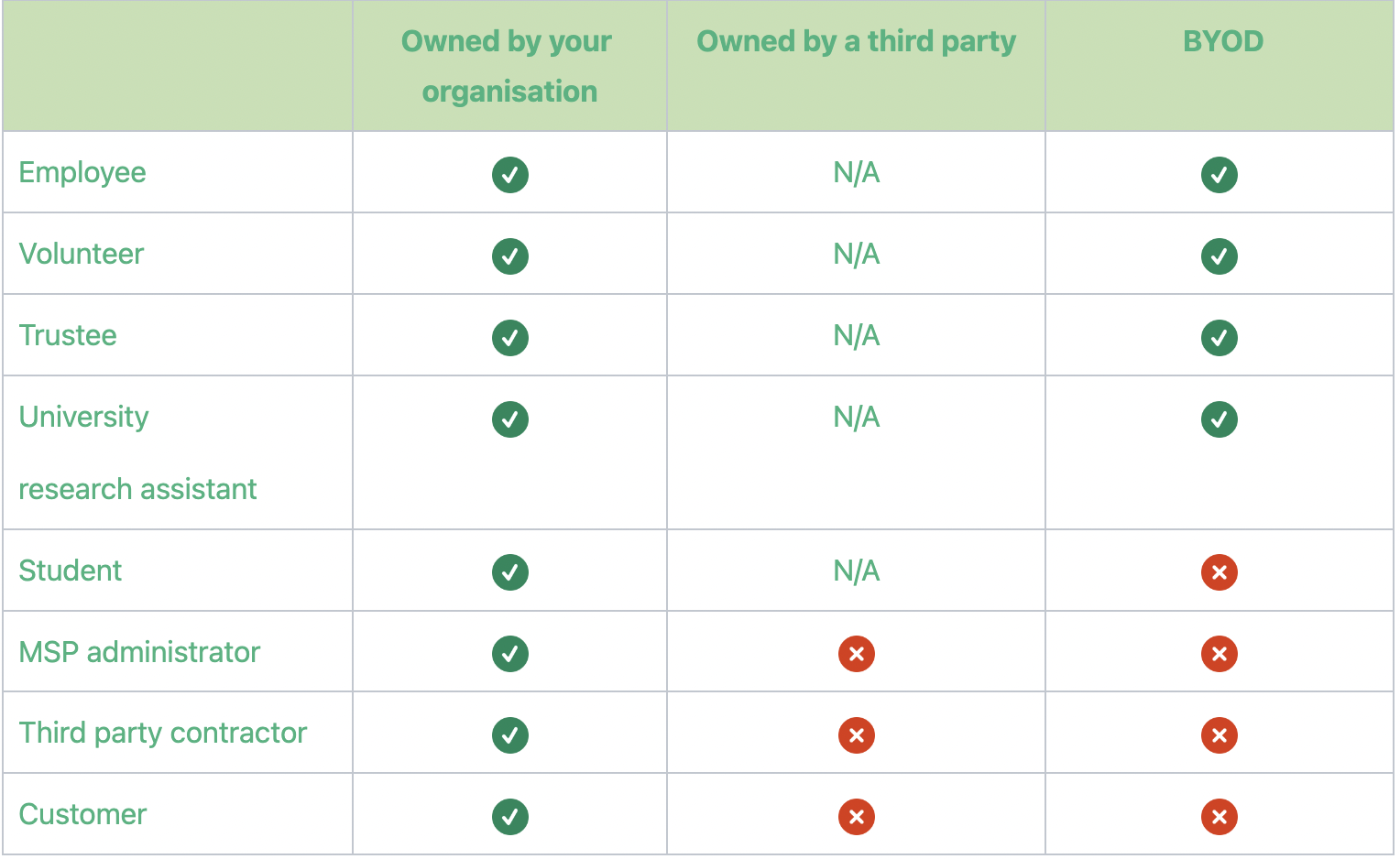 Source: IASME
Source: IASME
Why was the change made?
The new table provides clear guidance on the third-party devices within the scope of Cyber Essentials. It aims to address common queries regarding consultants, volunteers, and the often-discussed student devices.
When a third-party device is marked with a green tick, it falls within the scope, requiring the applicant organisation to demonstrate adherence to the necessary controls through a combination of technical measures and written policies.
As an illustration, if an in-scope third-party BYOD (Bring Your Own Device) is connected to an organisation's Office 365, the organisation can implement a conditional access policy that ensures the device meets the supported operating system requirements before establishing a connection.
It's important to note that student devices not owned by the applicant organisation are not and have never been included in the scope.
Rest assured that their usage does not impact the Cyber Essentials assessment. Let's keep your organisation secure and compliant!
5. The 'Device Unlocking' section has recently been updated to address limitations imposed by certain vendors.
In cases where configurations cannot be modified, it is crucial to utilise the default settings provided by the vendor. This ensures seamless device unlocking and a smoother user experience.
Why was the change made?
Many applicants may come across a situation where their device does not allow them to meet the Cyber Essentials requirements due to limited configuration options.
An example of this is when a device locks after 10 failed sign-in attempts. Interestingly, Samsung, one of the world's leading smartphone providers, has set their minimum sign-in attempts at 15, without providing an option to change this number.
In such cases, Cyber Essentials necessitates that applicants adhere to the device's minimum number of sign-in attempts before it locks.
6. Updated 'Malware Protection' Section
To ensure the security of your devices, it is crucial to have an active malware protection mechanism in place.
You have multiple options to choose from, as listed below. Most modern products come equipped with these options integrated into the software.
Alternatively, you also have the option to purchase third-party solutions. Regardless of your choice, it is essential to keep the software active, regularly update it following the vendor's instructions, and configure it as outlined below:
1. Anti-malware software (for Windows or MacOS devices, including servers, desktop computers, and laptops)
When using anti-malware software to safeguard your device, it should be configured to:
- Stay updated according to the vendor's recommendations
- Prevent the execution of malware
- Stop malicious code from running
- Block connections to malicious websites on the internet
2. Application allow listing (for all devices)
To maintain control over the applications running on your devices, it is recommended to implement application allow listing. The following guidelines should be followed:
- Actively approve applications before deploying them to devices
- Maintain an updated list of approved applications, ensuring that users cannot
- install any unsigned or applications with invalid signatures.
By adhering to these guidelines, you can enhance the security and protect the integrity of your devices and data.
Why was the change made?
There have been some concerns raised regarding the effectiveness of certain controls in safeguarding against malware.
To address this, we have updated our requirements with the latest insights, research, and recommendations from vendors.
By doing so, we aim to provide you with a more robust defence against potential threats.
7. Zero Trust Architecture and its impact on Cyber Essentials
The landscape of network architecture is evolving rapidly. With an increasing number of services transitioning to the cloud and the constant growth of Software as a Service (SaaS), it is crucial to adapt to these changes.
Moreover, organisations today are embracing flexible working arrangements, resulting in various device types connecting to systems from different locations.
Collaborating with partners and granting access to guest users has also become common practice, necessitating the need for more refined access control policies.
To address these challenges, the concept of Zero Trust Architecture has emerged.
By removing inherent trust in the network, this approach transforms system design. Instead, each access request is rigorously verified based on an access policy.
To ensure confidence in each request, robust authentication, authorisation, device health, and data value are taken into consideration.
Implementing Zero Trust Architecture not only enhances the user experience for remote access and data sharing but also strengthens the overall security posture.
By acknowledging the changing landscape and adopting this approach, organisations can better adapt to evolving cyber threats and protect their valuable assets.
So, are you ready to embrace the transformative power of Zero Trust Architecture for a more secure future?
The National Cyber Security Centre (NCSC) and IASME have taken into account the compatibility between Cyber Essentials and the zero trust architecture models.
It's important to note that implementing the technical controls of Cyber Essentials does not hinder you from adopting a zero trust architecture, as defined by the guidance provided by the NCSC.
Rest assured, both approaches can work hand in hand to bolster your cybersecurity measures and safeguard your digital assets.
8. The illustrative specification document updates, published on January 23rd 2023
We have exciting news about CE+! The illustrative specification document has undergone some updates, which were published on January 23rd.
These updates mainly focus on malware protection and how CE+ Assessors perform malware protection tests. During a CE+ audit, our Assessors will provide further details if needed.
9. Style and language adjustments to enhance the document's readability
But that's not all! We've also made several style and language adjustments to enhance the document's readability.
We've taken great care to ensure it aligns with plain English and accessibility guidelines.
10. Technical controls to match the self-assessment question set
In order to provide a more user-friendly experience, we've reordered the technical controls to match the self-assessment question set.
Now, the scheme requirements follow the same sequence as the question set: firewalls, secure configuration, security update management, user access controls, and malware protection.
We believe these improvements will make your CE+ journey smoother and more enjoyable.
If you would like any extra support, check out our free Cyber Security Assessment.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)






