The BBC reported that 74% of firms surveyed by the Institute of Directors plan on maintaining remote working. With 5-days a week in the office, appearing to be a thing of the past, businesses can no longer rely on the temporary security measures they had put in place in March 2020.
57% of employees were not provided with corporate devices
In June 2020, Kaspersky found that 57% of employees were not provided with corporate devices and only 34% of employees were given any IT security requirements to work securely on personal devices. IBM reported that 95% of cybersecurity breaches are caused by employee error, which includes lost or stolen devices, downloading malicious software and data breaches through using personal devices to access company data.
Before 2020, these types of matters would be the responsibilities of experienced and knowledgeable IT teams. However, with fewer and fewer companies returning to the office full-time, it is now up to employees to ensure they are working in a secure and protected manner.
With some much information out there, knowing where to start to protect your company can be overwhelming. Therefore, we have put together our top tips on how best to protect your business data whilst your staff are working remotely.
Are your employees starting to return to the office? We have a blog for that too. Read it here.
Download our 90-step IT Security Checklist...
- Identify potential threats and vulnerabilities so you can mitigate the risk and save your organisation both money and reputational damage if a breach does occur…
- Avoid data breaches that could have both a financial and reputational cost…
- Avoid regulatory issues if your customer data is stolen because you failed to comply with data protection laws.
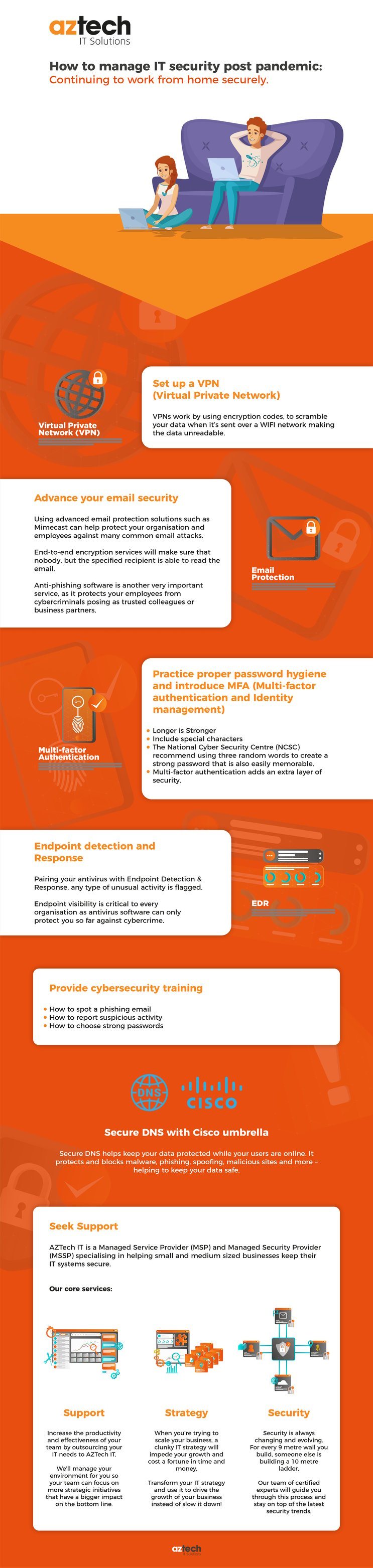
Ensure you have a secure VPN (Virtual Private Network)
A VPN is an essential tool for those undertaking any kind of secure remote work. As well as keeping your online activity private, a VPN service will establish a highly secure, encrypted connection to any Wi-Fi network. This means that any data sent or received over that network is fully protected.
This is critical for any employee who chooses to work in a public space, such as a coffee shop or library. VPNs also offer greater security than a standard password-secured Wi-Fi network, so they should be considered for those working from their own home too.

Introduce Advanced Email Security
Emails are a vital part of every business, and you wouldn’t want yours to end up in the wrong hands. There are a few different ways to protect your line of communication. Using advanced email protection solutions such as Mimecast can help protect your organisation and employees against many common email attacks. End-to-end encryption services will make sure that nobody but the specified recipient can read the email.
Anti-phishing software is another very important service, as it protects your employees from cybercriminals posing as trusted colleagues or business partners. These attacks often end in sensitive data being shared or malware being installed on the employee’s computer, resulting in further data breaches.
MFA – Multi-Factor Authentication & Identity Management
Cyber criminals often attempt to use weak or stolen passwords to gain access to web applications. Ensuring MFA is enabled on your corporate applications will add a layer of defence and mitigate a high number of potential breaches.
Learn more about Multi-Factor Authentication.
Cyber Security Awareness Training
It is now commonly understood that many of the successful network breaches are caused by a user error. Every employer and employee can benefit from more cybersecurity training.
This training can help your employees spot potential phishing scams, recognise if they have malware on their computers, and brief them on how to report any possible security threats.
It’s also a good idea to use these sessions to remind employees of your company’s specific IT security policies, and any applicable data privacy regulations (GDPR, for example).
This helps your workers create a secure remote working environment that is on par with being in the office.
Endpoint Detection & Response
Unfortunately, traditional antivirus software is not enough to protect your organisation on its own anymore. A traditional antivirus will periodically scan your computer, recognising malicious files based on a ‘signature’ the specific threat carries, but as we have seen in the past, there are many types of Malware that are hard to detect with traditional methods.
For example, file-less malware that operates in your computer’s memory is hidden from malware signature scanners. Due to the rapid evolution of technology, we are constantly adding to our endpoints, whether it’s desktops, smartphones or even the Internet of Things (IoT) - there are countless ways for cybercriminals to gain access to our data.
By pairing your antivirus with Endpoint Detection & Response, any type of unusual activity is flagged.
EDR monitors your endpoints and keeps a log of ‘normal activity, so when anything abnormal is detected, your security team is notified and they can investigate further.
This way any type of malware, whether it’s hidden from malware signature scanners or easily detected, will be investigated, isolated and removed, so your business can continue as usual.
Endpoint visibility is critical to every organisation as antivirus software can only protect you so far against cybercrime. It provides you with real-time visibility, rather than a periodic scan that may miss malicious activity.

Secure DNS with Cisco Umbrella
Cisco has said, "The Domain Name Service (DNS) is often referred to as the 'phone book' of the Internet. Every computer connected to the Internet identifies itself with an “Internet Protocol” or “IP” address, which is a series of numbers. All servers that host websites and apps have IP addresses, too."
Secure DNS and Content Security solutions provide your first line of defence against threats on the internet, delivering complete visibility into internet activity across all locations, devices and users - blocking threats before they've reached your network and endpoints.
Secure DNS helps keep your data protected while your users are online. It protects and blocks malware, phishing, spoofing, malicious sites and more – helping to keep your data safe.
You need to be able to let your users work online safely wherever they are, without putting your data at risk. As cybercrime attacks become more advanced with data breaches occurring through email and web sources, your security protection needs to evolve as well.
Seek Support
AZTech IT is a Managed Service Provider (MSP) and Managed Security Provider (MSSP) specialising in helping small and medium-sized businesses keep their IT systems secure. We offer a free IT Security Assessment, analysing your current security tools and advising you of any gaps that need to be plugged in.

-1.png?width=552&height=678&name=text-image%20module%20desktop%20(4)-1.png)


.png?width=2000&name=Case%20study%20(21).png)


-2.png?width=422&height=591&name=text%20image%20tablet%20(31)-2.png)












